Unlocking Vulnrichment: Enriching CVE Data
In today’s fast-paced cybersecurity landscape, staying ahead of vulnerabilities is a daily race against time. Every day, dozens to hundreds of new CVEs (Common Vulnerabilities and Exposures) are published, many of which affect critical systems. But let’s face it, simply knowing a vulnerability exists is rarely enough to act. As cybersecurity practitioners, researchers, and defenders, we need context. We need clarity. And most importantly, we need actionable insights that can help prioritize patching efforts and mitigate risks.
To that end, you may recall CISA’s May 10, 2024 announcement establishing Vulnrichment, our initiative to supercharge CVE data with context, scoring, and analysis that go beyond the basics. This post is a mid-year check-in to briefly cover the how’s and why’s of this effort, now that we’ve been running it for a few months.
A Power-Up for CVE Data
If you’re an IT defender or a vulnerability management pro, CISA’s Vulnrichment project can make your life easier. It enriches basic CVE data with actionable insights like Stakeholder-Specific Vulnerability Categorization (SSVC) decision points, Common Weakness Enumeration (CWE) IDs, and Common Vulnerability Scoring System (CVSS), all bundled into the CVE records you’re already pulling. Think of it as a turbocharged upgrade to the CVE data you’re already consuming. Best part? You don’t need to set up anything new—this enriched data is automatically baked into the CVE feeds you’re already using.
You’re soaking in it!
Today, all Vulnrichment data ends up in the Authorized Data Publisher (ADP) container for individual CVEs, so if you’re pulling CVE data from https://cve.org via the API, or from GitHub at https://github.com/CVEProject/cvelistV5 , you’re already collecting Vulnrichment data. It’s just a matter of parsing it out. Here’s an example:
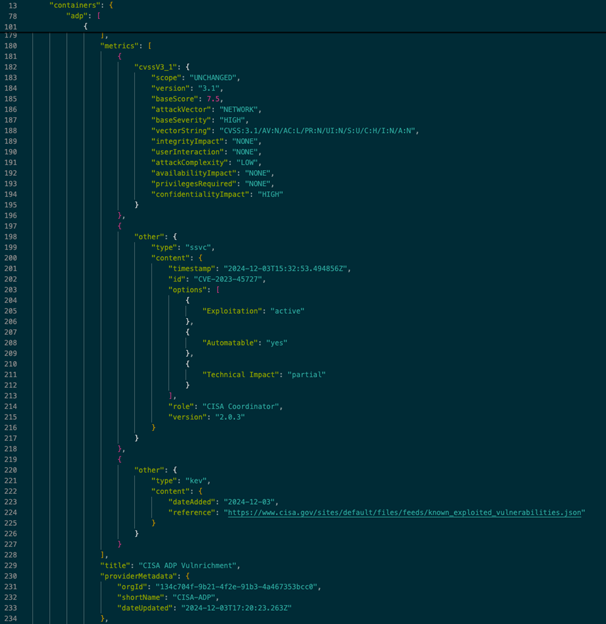
This is for CVE-2023-45727, selected because it’s a recent KEV entry that has a full Vulnrichment ADP container. Let’s say you wanted to query the “Exploitation” field of the CISA-provided SSVC decision points. You’d iterate over the ADP container, look for the Vulnrichment ADP container, look for the SSVC decision point, and then return the value for “exploitation.” Using the command line tool jq as an example, that might look like this:
jq -r '.containers.adp[] | select(.title == "CISA ADP Vulnrichment") | .metrics[]?.other? | select(.type == "ssvc") | .content.options[]? | select(.Exploitation) | .Exploitation' CVE-2023-45727.json
active
This query will return one of “active,” “poc,” or “none.”
Found a problem?
Let’s say you’re happily parsing all this Vulnrichment data, but you found a mistake in one, like the wrong CWE assigned in the Vulnrichment container. Taking CVE-2023-45727 again as the example, let’s pretend that CISA accidentally assigned CWE-610, “Externally Controlled Reference to a Resource in Another Sphere,” when it really should be CWE-611, “Improper Restriction of XML External Entity Reference.” Instead of just gnashing your teeth and wondering how we could be so foolish, you are invited to open an issue at GitHub (specifically, at https://github.com/cisagov/vulnrichment/issues ) and tell us about it, like so:
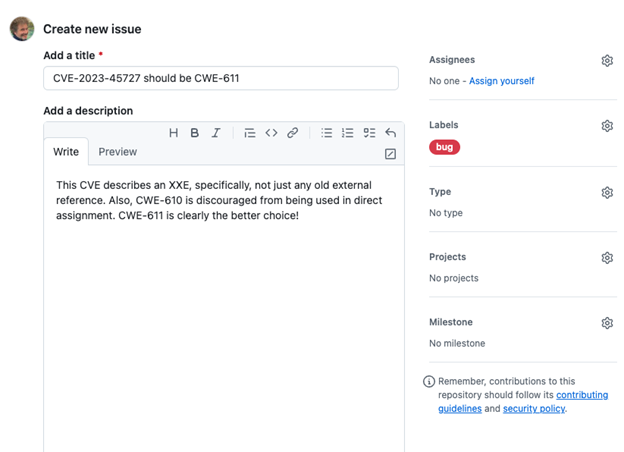
We take our inbound issues pretty seriously and aim to have them resolved quickly. These kinds of bug reports make Vulnrichment not only an authoritative source of truth about CVEs, but a responsive source, as well.
The Value of Vulnrichment
If you’re consuming CVE data – and if you’ve read this far, chances are pretty good you are – you’re probably already using the regular CVE APIs. But, unless you’re parsing out the ADP container, you’re missing out on some key benefits. Here’s why:
- Clarity and Actionability: CVE data can be… a bit sparse. Simply knowing that a vulnerability exists doesn’t tell you whether it’s been exploited in the wild, if user interaction is required to exploit it, or what vectors are available to attackers. With Vulnrichment, CISA adds broad context in the form of SSVC decision points that help you understand the exploitability, impact, and automatability of a vulnerability. This additional layer of intelligence lets you prioritize remediation based on actual threat risk.
- Prioritization On Easy Mode: With Vulnrichment, vulnerabilities are enriched with actionable data points like Exploitability (Is there a public exploit? Is it actively being used in the wild?), Technical Impact (Is this vulnerability likely to grant full control over your system, or mere information disclosure?) and Automatability (Can attackers exploit this vulnerability at will, or does it require some setup every time?). This makes the question of “What should I patch first?” a whole lot easier to answer. These all come under the “SSVC” section of the ADP container, which you can learn more about at https://cisa.gov/ssvc, as well as a future blog post dedicated to CISA’s use and advocacy for SSVC!
- Confidence in Your Data: Vulnrichment ensures that the CVE data you’re working with is more accurate and complete. If the data provided by the original CVE Numbering Authority (CNA) didn’t provide some key data points, CISA fills in the gaps, adding CWE Identifiers and CVSS scores when it’s possible to determine those. If the CVE is later updated by the issuing CNA with more direct information, CISA’s contribution will be removed to avoid confusing conflicts. All of this is to say that when you’re looking at fresh CVE data, you know you’re always working with the best available intelligence about those vulnerabilities.
Friends, Admins, and Countrymen: Lend me your eyes!
“Given enough eyeballs, all bugs are shallow,” quipped Eric S. Raymond in the seminal The Cathedral and the Bazaar, and we here at CISA believe we’ve built a pretty good eyeball-attractor with Vulnrichment.
Of course, this is more than just an academic project. We’re not here to merely admire the problems inherent in sharing vulnerability information and prioritizing patching efforts. Vulnrichment is an ongoing, operational effort to make CVE data more useful, actionable, and accurate for everyone. By adding CISA’s unique operational context, scoring, and more detailed analysis to CVEs, CISA hopes to enrich the growing CVE corpus and create a dynamic, living resource that helps security professionals make smarter decisions faster. So, whether you’re a researcher, a security analyst, or an enterprise IT manager, take a look at what Vulnrichment has to offer, and if you’re so inclined, offer your opinions on how to make it even better.
Ready to get started? Head over to the Vulnrichment GitHub repo and get ready to level up your vulnerability management game.




