BOD 23-02: Implementation Guidance for Mitigating the Risk from Internet-Exposed Management Interfaces
Background
On June 13, 2023, CISA issued Binding Operational Directive 23-02: Mitigating the Risk from Internet-Exposed Management Interfaces. The Directive requires federal civilian executive branch (FCEB) agencies to take steps to reduce their attack surface created by insecure or misconfigured management interfaces across certain classes of devices.
The requirements in this Directive apply only to devices meeting BOTH of the following criteria:
- Devices residing on or supporting federal information systems and/or networks that belong to one of the following classes: routers, switches, firewalls, VPN concentrators, proxies, load balancers, and out of band server management interfaces (such as iLo and iDRAC).
- Devices for which the management interfaces are using network protocols for remote management over public internet, including, but not limited to: Hypertext Transfer Protocol (HTTP), Hypertext Transfer Protocol Secure (HTTPS), File Transfer Protocol (FTP), , Simple Network Management Protocol (SNMP), Teletype Network (Telnet), Trivial File Transfer Protocol (TFTP), Remote Desktop Protocol (RDP), Remote Login (rlogin), Remote Shell (RSH), Secure Shell (SSH), Server Message Block (SMB), Virtual Network Computing (VNC), and X11 (X Window System).
Frequently Asked Questions
Q: What is the difference between “network” vs. “networked” management interfaces?
A: In order to avoid confusion and to clearly define the scope, this Directive defines “networked management interfaces” as interfaces that are accessible over network protocols and are meant exclusively for authorized users to perform administrative activities on a device, a group of devices, or the network itself. “Network” interfaces may be interpreted as limited to management of networks only.
Q: What do you mean by “networked management interface?”
A: In the context of this Directive, a “networked management interface” is a device interface dedicated to configuration and management operations (meant exclusively for authorized users to perform administrative activities on a device, a group of devices, or the network itself, and is accessible from a network over a network protocol). Other terms used to describe these types of interfaces include management interface, administrative (admin) interface, and “back end” interface. Management interfaces are typically connected to dedicated out of band management networks via a dedicated management port.
Q: Are the serial ports used to access the command line interface directly within the scope of this Directive?
A: Serial ports used to access the command line interface directly do not inherently fall within the scope unless those serial ports are exposed on the network via a console server.
Q: Can you provide an example of a networked management interface in scope?
A: An agency employs a router that manages traffic inside their network. The router’s web management interface, used by an agency administrator, is accessible via HTTPS. The management interface is reachable by an entity directly from the public-facing internet. In this example, the management interface would fit the scope of the BOD and will be subject to the Required Actions.
Q: Can CISA provide sample diagrams for the most common use cases to which this Directive applies?
A: These logical diagrams illustrate some of the most common use cases, along with recommended solutions. Please note that these logical diagrams are not prescriptive, only represent the most common use cases, and do not reflect physical implementations.
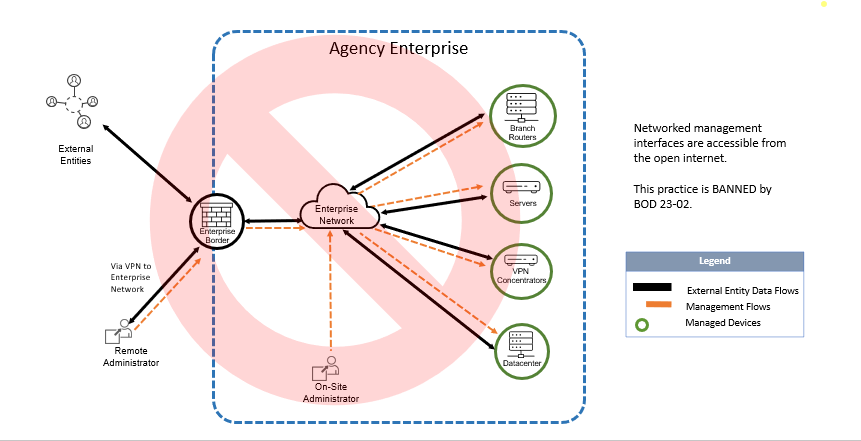
Figure 1 - Practice banned by BOD 23-02 – networked management interfaces accessible from the internet.
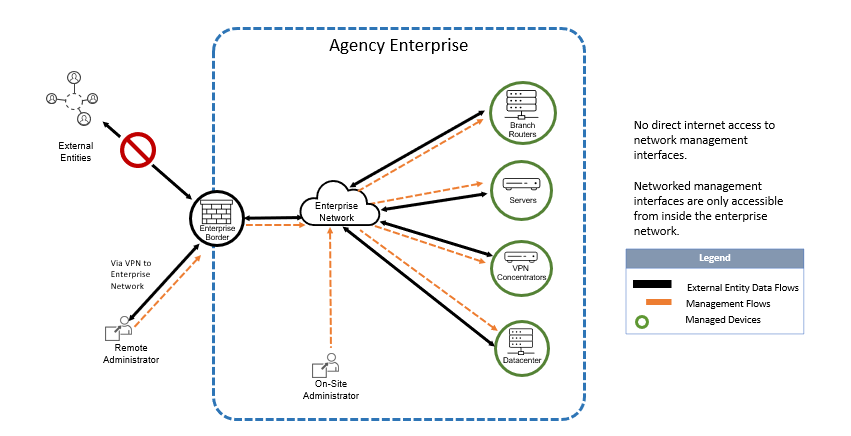
Figure 2 - Acceptable use case – networked management interfaces only accessible from inside the enterprise network.
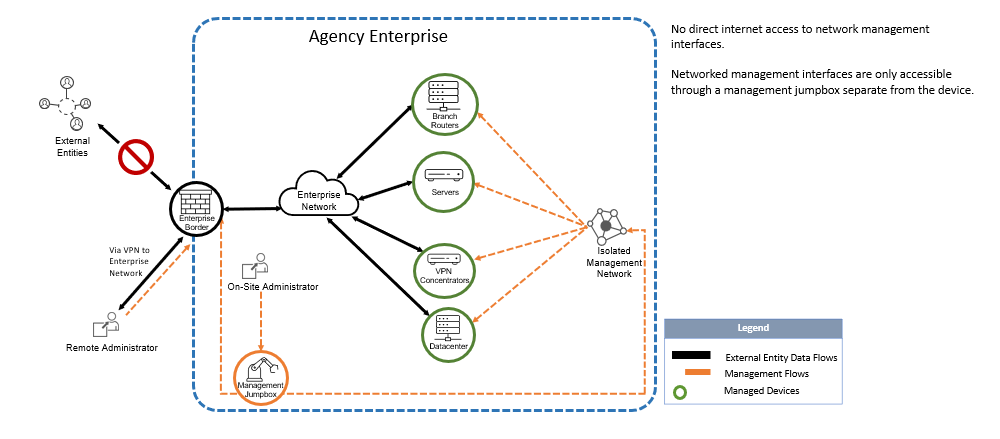
Figure 3 - Acceptable use case – networked management interfaces only accessible from management network through management jumpbox.
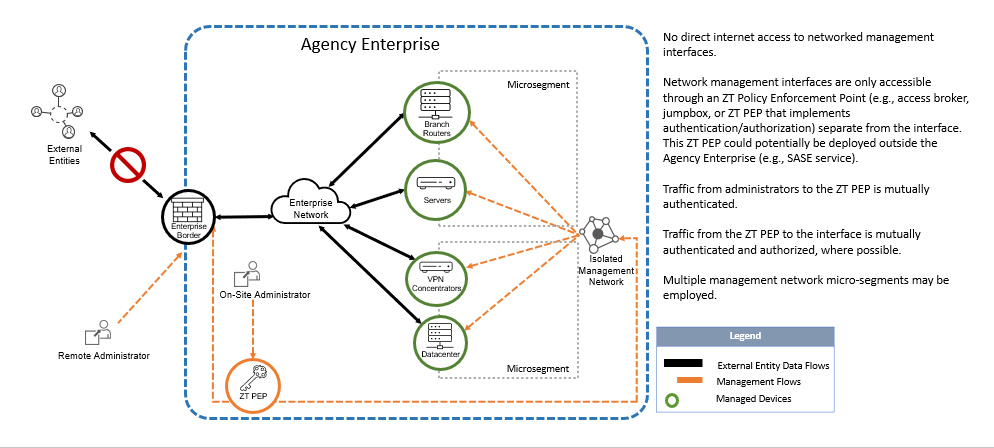
Figure 4 - Acceptable use case – networked management interfaces only accessible from management network micro-segments through ZT PEP.
Q: What does CISA consider an “out of band server management interface?”
A: An “out of band server management interface” refers to proprietary interfaces used for remote control of servers that are accessed via a dedicated network connection. CISA does not limit this definition to one specific vendor. For example, HP’s Integrated Lights-Out (iLo) management software, while proprietary, would fit the scope of this Directive. Another example would be the Integrated Dell Remote Access Controller (iDRAC). These out of band interfaces should never be directly accessible via the public internet.
Q: Does this Directive apply to contractor systems?
A: The Directive applies to all federal information systems hosted by government or upon its behalf.
Q: Does the Directive apply to cloud systems?
A: The Directive applies to all devices inventoried in FISMA authorization boundaries. In most instances, this will include devices in IaaS and possibly PaaS boundary. By definition, the SaaS boundary does not include device inventories; therefore, it is unlikely that a SaaS system would fall within the scope.
Q: What qualifies as removal from the internet?
A: Most physical or logical controls that prevent direct access to the networked management interface from the internet will satisfy this requirement. This includes, but is not limited to, physically removing the management interfaces from internet accessible networks, using VLANs, internal (non-internet routable) IP addresses, firewalls, and deployment of Zero Trust architecture capabilities.
Q: Agencies must take at least one of two possible options—remove the interface from the internet and/or protect it with Zero Trust aligned capabilities. Does CISA have a preference?
A: CISA strongly encourages agencies to implement Zero Trust concepts where technically feasible. These concepts can be found in OMB M-22-09, NIST 800-207, the TIC 3.0 Capability Catalog, and CISA's Zero Trust Maturity Model. However, CISA also understands that due to short remediation timeline requirements, it may be quicker and more efficient to remove the interface from the public-facing internet as a first step.
Q: For Zero Trust Architecture capabilities does CISA require the policy enforcement point to be separate from the device itself?
A: The policy enforcement should be separate from the device itself in order to provide protection against vulnerabilities or compromise in the management interface. Some devices host their own policy enforcement points (PEP) on the device itself, which can be used to provide finer grained policy and access to the device’s management interface. However, a separate policy enforcement point should be used to provide the first line of defense in a defense in depth strategy. Two examples of separate policy enforcement points could be SASE-based private access solutions or access proxies.
Q: Does this Directive conflict with OMB 22-09 Federal Zero Trust Strategy requirements?
A: No, this Directive is aligned with both OMB and CISA’s vision for Zero Trust. The Directive complements the Federal Zero Trust Strategy and encourages agencies to implement Zero Trust principles.
Q: What concepts of Zero Trust is CISA looking for?
A: CISA strongly encourages users and administrators to review documentation provided regarding Zero Trust: OMB M-22-09, NIST 800-207, the TIC 3.0 Capability Catalog, and CISA's Zero Trust Maturity Model. Some elements to a successful Zero Trust environment contain, but are not limited to:
- Multifactor authentication (MFA)
- Asset management and identification
- Isolation of critical workloads and strong access policy
- Encryption of data in transit
These elements should not be considered a finite list.
Q: Are honeypot hosts within the scope of the Binding Operational Directive?
A: While honeypot hosts are designed to look like agency networks to entice attackers, malicious actions against a properly configured honeypot host would not be able to damage an agency. Networked management interfaces on honeypot devices are still within scope.
Q: Are satellite locations with small office/home office devices within the scope?
A: Yes. All federal information systems are in scope.
Q: Does my agency need to identify and inventory all networked management interfaces that fall in scope?
A: The Binding Operational Directive does not include a provision that requires agencies to identify, inventory, and report all networked management interfaces in scope. However, CISA expects that agencies have processes in place to identify and inventory all networked management interfaces as part of a comprehensive asset management policy and strategy.
As noted in the Implementation Guidance for BOD 23-01, asset management “is the active monitoring and administration of endpoints using a centralized solution, such as unified endpoint management (UEM), mobile device management (MDM), or enterprise mobility management (EMM). Inventories from asset management solutions may be used to feed the information about agency assets into the results of a comprehensive asset discovery effort.”
Q: When will CISA begin to provide reports to agencies identifying devices that fall within the scope that may be on the public facing internet?
A: Within 30 days.
Q: Can you provide examples of management and technical controls required to comply with section 2 of the Directive?
A: At the minimum, agencies are expected to have policies (management controls) in place that require all management interfaces on existing and newly added devices, identified as in scope for this Directive, have at least one of the required protections in place. Wherever technically feasible, agencies should also have automated ways (technical controls) to scan for and discover interfaces in scope of this Directive.
Q: What if my agency cannot mitigate an identified interface within 14 days due to technical or operational reasons?
A: Agencies should notify CISA immediately of any instances where they don’t anticipate meeting required deadlines through CyberDirectives@mail.cisa.dhs.gov and will need to complete and submit to CISA a standard remediation plan template within the 14-day required timeframe.
Q: Will CISA notify my agency if scanning returns negative results?
A: No. If CISA scans are negative, agencies will not receive a notification from CISA stating such. If CISA scanning discovers a device within the scope of the Directive, agencies will be notified of positive findings through CyberScope.
Q: Does this BOD conflict with vendors’ configuration and hardening guidelines?
A: A Binding Operational Directive is a compulsory direction to federal civilian executive branch agencies for purposes of safeguarding federal information and information systems. The intent is not to conflict with product vendor recommendations but to complement the existing hardening recommendations. Most vendors include guidance on how to prevent exposure of these interfaces to the public-facing internet. For general information, assistance, and reporting, please contact CyberDirectives@mail.cisa.dhs.gov.




