BOD 25-01: Implementation Guidance for Implementing Secure Practices for Cloud Services

Updated: May 27, 2025
Note: CISA will update this page to provide users and Agencies with the latest information and guidance on BOD implementation.
Background
Malicious threat actors have increasingly targeted cloud environments and evolved tactics to gain initial cloud access. In recent cybersecurity incidents, the improper configuration of security controls in cloud environments introduced substantial risk and resulted in actual compromises. To combat these threats, the Cybersecurity and Infrastructure Security Agency (CISA) initiated the Secure Cloud Business Applications (SCuBA) project. Through the SCuBA project, CISA developed Secure Configuration Baselines, providing consistent and manageable cloud security configurations and assessment tools, allowing agencies and CISA to improve security for Federal Civilian Executive Branch (FCEB) assets hosted in cloud environments. Binding Operational Directive (BOD) 25-01 requires agencies to implement a set of SCuBA Secure Configuration Baselines for certain Software as a Service (SaaS) products widely used in the FCEB, deploy CISA-developed automated configuration assessment tools to measure against the required baselines, integrate with CISA’s continuous monitoring infrastructure, and remediate deviations from the secure configuration baselines. These steps reduce risks highlighted by recent adversary activity and increase resiliency for FCEB agencies against cyber threats.
This Implementation Guidance provides FCEB Agencies with additional context and instructions for implementing the requirements from BOD 25-01.
Scope
BOD 25-01 applies to all production or operational cloud tenants (operating in or as federal information systems) with associated and finalized SCuBA Secure Configuration Baselines published by CISA. At the time of issuance of BOD 25-01, CISA published final SCuBA Secure Cloud Configuration Baselines for Microsoft Office 365 (M365). In the future, CISA may release additional SCuBA Secure Configuration Baselines for other cloud products. Upon issuance of applicable baselines, such products will fall under the scope of this Directive. Any baselines not updated within one year will automatically fall out of scope and will be removed from the SCuBA Secure Configuration Baseline catalog, linked through the Binding Operational Directive 25-01 Required Configurations website.
BOD 25-01 requirements pertain only to mandatory policies referenced within the SCuBA Secure Configuration Baselines as “shall” actions. All such mandatory policies are published on the Binding Operational Directive 25-01 Required Configurations website. SCuBA Secure Configuration Baselines specify both recommended policies that are left to Agency discretion to implement (identified as “should” actions within the baselines) and mandatory SCuBA policies that must be implemented.
Scope Clarification
The scope of BOD 25-01 has several parts, including addressing production and operational content, operating in or as federal information systems, using finalized SCuBA Secure Configuration Baselines published by CISA, and ensuring mandatory policy implementation. As Agencies evaluate whether cloud service tenancies are in scope of the BOD’s requirements, they should consider the following guidance and how it applies to their situation:
- Production or operational tenant: A production or operational tenant is a Cloud Service Provider (CSP) environment used by the government to conduct official government business, whether operated by the government or a contractor. A tenant is not a production or operational tenant if it is primarily used to test configuration changes before application to another tenant or as part of the software development and testing process before it is deployed to another tenant. Agencies may choose to include additional tenants – those not included in the BOD’s scope – in CISA’s continuous monitoring program at their discretion.
- Operating in or as federal information systems: The scope of the BOD is limited to tenants that are part of an Information System, as defined in 44 USC § 3502(8), that is owned by or operated by Federal Agency or on behalf of a Federal Agency by a contractor. Tenants outside of the authorization boundary of an Agency’s information system are not in scope of the BOD.
- Finalized SCuBA Secure Configuration Baselines published by CISA: The BOD’s scope is limited to cloud services that have a finalized SCuBA Secure Configuration Baseline published by CISA. At the time of BOD 25-01 issuance, M365 is the only finalized Secure Configuration Baseline. Secure Configuration Baselines are initially developed in a draft format and circulated for comment with agencies, vendors, and the public prior to becoming a finalized baseline. The Binding Operational Directive 25-01 Required Configurations website contains the authoritative list of finalized baselines and mandatory policies under the BOD.
- Mandatory policies: Requirement 3 of the BOD 25-01 mandates the implementation of “shall” policies from in-scope Secure Configuration Baselines. The authoritative list of mandatory policies and finalized baselines can be found on the Binding Operational Directive 25-01 Required Configurations website. Although recommended (“should”) policies are not required, CISA strongly advises agencies implement these policies to the greatest extent possible in their environment.
- Service model: At this time, the scope of the BOD is limited to SaaS. As such, both Platform as a Service (PaaS) and Infrastructure as a Service (IaaS) are out of scope (see National Institute of Standards and Technology (NIST) Special Publication (SP) 800-145 for definitions). Importantly, this means tenants created for Azure Subscriptions that do not use M365 services are out of scope. Even though Azure subscriptions and M365 rely on the same identity provider (Microsoft Entra ID), as Azure is a PaaS/IaaS platform, Azure IaaS has additional security requirements that are not adequately covered by the current M365 baselines.
Component Coordination
Prior to reporting, all sub-components should coordinate with their top-level Department. Manual reporting in CyberScope is typically submitted by Department-level POCs. CyberScope accounts also require approval from Agency specific Department-level POCs. If Agencies need help in identifying their Department-level point of contact (POC) to approve their account request, they should reach out to CyberScopeHelp@mail.cisa.dhs.gov.
Methods of Compliance and Reporting
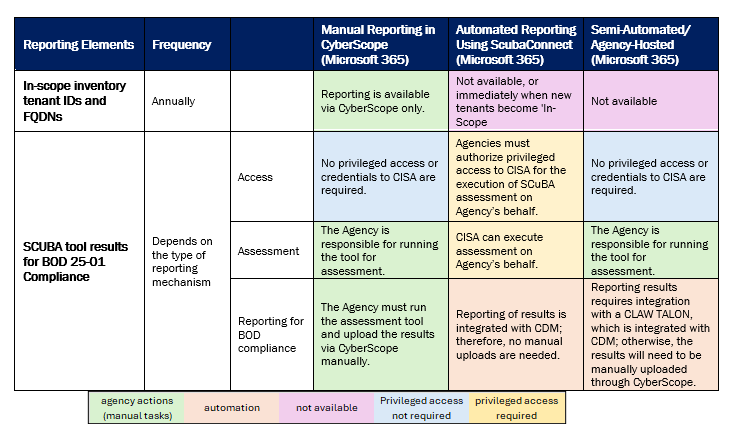
To meet reporting requirements, there are three reporting options available for Agencies:
- Agencies can manually report via CyberScope;
- Agencies can opt in for automated reporting with the CISA-hosted ScubaConnect tool; or
- Agencies can report using an Agency-hosted model (semi-automated) where they host their own ScubaConnect instance and integrate with Continuous Diagnostics and Mitigation (CDM) using a CLAW TALON.
Please note that Agencies can choose how they report compliance using any of these three methods. Agencies should choose which option works best for their environment, in coordination with their top-level Department and proceed to the section in the Implementation Guidance on how to accomplish the BOD requirements for the reporting method chosen.
- Instructions for Manual Reporting in CyberScope (Microsoft 365)
-
Manual Reporting in CyberScope
Requirement #1
Identify all cloud tenants within the scope of this Directive:
1. No later than Friday, February 21, 2025, provide the tenant name (Tenant ID and fully qualified domain name [FQDN]) and the system-owning Agency/component for each tenant, following CISA reporting instructions.
2. Update this inventory in the first quarter annually by following CISA reporting instructions.
- The CyberScope SCuBA Tenant Inventory site, an interactive CyberScope user interface (U/I) available in December 2024. Agencies may begin collecting the inventory in an CyberScope Excel template, currently available via CyberScope.
- Agencies must update their inventory by the end of the first quarter of each fiscal year. The inventory list will be used to help ensure reports for all tenants are being received in a timely manner. Agencies are encouraged to update their inventory immediately when there are changes to tenants. Agencies may complete this requirement manually or with assistance from the output of the ScubaGear tool.
- To access the CyberScope SCuBA Tenant Inventory website, log into an Agency MAX ID account using a registered PIV or CAC card or with a MAX.gov UserID and password.
- To register a MAX ID with CyberScope, register and select “Sign Up” when prompted and select or enter the following:
- Agency: Select the appropriate Agency from the dropdown menu.
- Request Access: Select “Binding Operational Directive 25-01”
-
Work Phone: Enter the user’s work phone number in the format 000-000-0000.
NOTE: CyberScope accounts require approval from Agency specific Department-level POCs. Please coordinate with your component’s top-level Department.
- For users possessing a CyberScope account but not access to the SCuBA Tenant Inventory page, request access by reaching out to the Agency Lead POC or the CyberScope Help Desk (cyberscopehelp@mail.cisa.dhs.gov) to assign the SCuBA BOD Data Entry/Validate and/or Submitter permissions to the CyberScope account.
- To register a MAX ID with CyberScope, register and select “Sign Up” when prompted and select or enter the following:
- With access to the CyberScope SCuBA Tenant Inventory site, select “Add New Tenant.” Then, select or enter the following for all M365 cloud tenants within the scope of this Directive:
- Bureau/Sub-Component: Select the bureau or sub-component that the tenant is operated for. (Each user is already assigned to an Agency; therefore, CyberScope is aware of this context, and all tenants added by a user will be assigned to the Agency. The Bureau/Sub-Component list will be limited to the user’s Agency. Example: If a user’s component was CISA under the Department of Homeland Security (DHS), the user’s Agency is DHS; the bureau or sub-component would be CISA. If the tenant was operated by DHS HQ, no bureau or sub-component would be selected.)
- If no sub-component, insert Agency name.
- Product: Select M365.
- Service Plan: For M365, select either Commercial, GCC, or GCC High.
- Tenant ID: Enter the globally unique identifier (GUID) for the tenant.
- Microsoft Entra admin center:
- Sign in to the Microsoft Entra admin center as at least a Global Reader.
- Browse to Identity > Overview > Properties.
- Scroll down to the Tenant ID section to find the tenant ID in the box.
- Azure Portal
- Sign in to the Azure portal.
- Browse to Microsoft Entra ID > Properties.
- Scroll down to the Tenant ID section to find the tenant ID listed.
- Other: PowerShell, Azure, or M365 command line interface (CLI)
- Follow the commands listed in How to find your tenant ID - Microsoft Entra | Microsoft Learn
- Microsoft Entra admin center:
- Tenant FQDN: Enter the FQDN for the tenant (e.g., cisa.onmicrosoft.com).
- Microsoft Entra admin center:
- Sign in to the Microsoft Entra admin center as at least a Global Reader.
- Browse to Identity > Overview
- Scroll down to the Primary Domain section to find the Tenant FQDN listed.
- Microsoft Entra admin center:
- In Scope: The default is “Y” (Yes) when entering a new tenant. If a tenant falls out of scope or an Agency is pre-emptively listing a tenant they know will soon be within the scope of the BOD, then change this value to “N” (No). Subsequently, CISA will know not to expect results from the tenant.
- When “N” (No) is selected, data for the associated tenant will be shown on a normal Agency dashboard, but will not be shown on the BOD 25-01 CDM dashboard or used for compliance.
- This option is included to allow Agencies flexibility in maintaining current inventory data:
- Agencies can use the CDM infrastructure to track their cloud tenants and view their inventories through their own CDM dashboards.
- Agencies can prepopulate inventories as they bring new tenants on-board and prepare for additional tenants entering the scope of the Directive.
- Agencies can adjust their inventory through a single field without having to delete and re-add data. For example, if a tenant is taken offline for a period of time but will re-enter production again at a later date.
- ATO: Select “Y” (Yes) if the tenant has an active Authorization to Operate (ATO).
- Bureau/Sub-Component: Select the bureau or sub-component that the tenant is operated for. (Each user is already assigned to an Agency; therefore, CyberScope is aware of this context, and all tenants added by a user will be assigned to the Agency. The Bureau/Sub-Component list will be limited to the user’s Agency. Example: If a user’s component was CISA under the Department of Homeland Security (DHS), the user’s Agency is DHS; the bureau or sub-component would be CISA. If the tenant was operated by DHS HQ, no bureau or sub-component would be selected.)
- Agencies can run ScubaGear on each M365 tenant to help fill out the CyberScope SCuBA Tenant Inventory fields. See Requirement #2 for information on running ScubaGear.
- To install and run ScubaGear, refer to the ScubaGear GitHub README. The README contains instructions to install ScubaGear from PowerShell Gallery. Find information on the ScubaGear reports in the ScubaGear documentation on GitHub.
- Note: CISA recognizes the varied internal Agency processes that must be followed to authorize software use on Agency networks. Agencies should initiate those processes as needed for ScubaGear and its dependencies.
Requirement #2
For Manual Reporting Selection: Deploy all SCuBA assessment tools for in-scope cloud tenants no later than Friday, April 25, 2025 and begin continuous reporting on the requirements of this Directive by manually reporting the results of the most recent SCuBA assessment tool version to CISA quarterly in a CISA-approved, machine-readable format, following CISA reporting instructions.
Note: Department sub-components should coordinate with their Agency top-level Departments. Manual reporting in CyberScope is typically submitted by Department-level POCs.
User Guidance: To achieve compliance, agencies will run ScubaGear on all in-scope tenants. Agencies may complete the remainder of this requirement in one of two ways. If your Agency has selected the manually reporting method, you will achieve this requirement by manual configuration of the assessment tool with a quarterly reporting obligation of Agency results to CISA.
Prior to selection, the following items are important to ensure proper configuration of the ScubaGear tool to run assessments:

- Within the ScubaGear Configuration File, Agencies should insert values for their Department-level Agency name in the “OrgName” of the config file and, if applicable, they should enter the sub-component, bureau, or subagency name in the “OrgUnitName” of the config file.
- Note: The “OrgName” should be the top-level Agency acronym as defined under CISA’s Federal Civilian Executive Branch Agency List. The “OrgUnitName” should be the next organization acronym one level down from the top level. Example below and link to a sample config file:
- E.g., OrgName: “DHS”
- E.g., OrgUnitName: “CISA” (if applicable)
- Note: If your bureau has a separate CDM deployment, you should have that bureau reported as OrgName. This does not apply for most customers. If OrgUnitName is not applicable, then enter OrgUnitName: “”
- Note: The “OrgName” should be the top-level Agency acronym as defined under CISA’s Federal Civilian Executive Branch Agency List. The “OrgUnitName” should be the next organization acronym one level down from the top level. Example below and link to a sample config file:
- Agency manually runs ScubaGear and reports the results to CISA by manually uploading them to CyberScope.
- In this option, agencies manually upload ScubaGear assessment results to CISA quarterly through CyberScope. Results will be updated in the CDM dashboard upon receipt by CISA. If desired, agencies may update results in CyberScope more frequently. For agencies manually reporting results, follow the steps in Requirement #1 to ensure all cloud tenants within the scope of this Directive have their required information collected and listed via CyberScope.
- Agencies must configure and run ScubaGear for all in-scope tenants.
- Refer to the ScubaGear GitHub README, which contains instructions to install ScubaGear from PowerShell Gallery.
- After running the ScubaGear tool for each in-scope tenant, log in to CyberScope and select the “v” symbol at the end of each row to open the submission section for the tenant.
- For Submission Type, select from the dropdown menu “Scan Results.”
- Select and submit the SCuBA assessment tool results by dragging and dropping the file or selecting browse and selecting the file. For the “Scan Results” requirement, the file type is limited to:
- .json: grab and drop or select via browse the ScubaResults .json file in the output directory folder. The ScubaResults file will include about 18 characters that are part of the UUID (unique identifier that is generated for each report; the full report unique identifier is available in the .json file) prior to the .json file extension. Do not alter the file name produced by the ScubaGear tool before submitting results to CyberScope.
- Agencies will then upload the resulting output via the BOD 25-01 CyberScope page.
- Agencies must configure and run ScubaGear for all in-scope tenants.
- In this option, agencies manually upload ScubaGear assessment results to CISA quarterly through CyberScope. Results will be updated in the CDM dashboard upon receipt by CISA. If desired, agencies may update results in CyberScope more frequently. For agencies manually reporting results, follow the steps in Requirement #1 to ensure all cloud tenants within the scope of this Directive have their required information collected and listed via CyberScope.
Requirement #3
Implement all mandatory SCuBA policies effective as of this Directive’s issuance, as set forth in the CISA-managed Binding Operational Directive 25-01 Required Configurations website no later than Friday, June 20, 2025. These mandatory SCuBA policies are provided on the Required Configurations website and correspond to the mandatory policies referenced within the SCuBA Secure Configuration Baselines.
User Guidance: When implementing mandatory policies to all cloud instances covered by this BOD, Agencies shall reference the Binding Operational Directive 25-01 Required Configurations website.
- Follow all steps identified in Requirements #1 and #2, verifying that:
- All cloud tenants within the scope of this Directive have been collected and entered on the CyberScope SCuBA Tenant Inventory site.
- SCuBA assessment tools for in-scope cloud tenants have been enrolled in the SCuBA continuous reporting solution or results submitted manually in the CyberScope SCuBA Tenant Inventory site.
- For the mandatory policies identified as “failures,” follow the next steps below:
- Open the file name BaselineReports.html to view the SCuBA M365 Secure Baseline Conformance Report.
- Review all mandatory policies referenced within the SCuBA Secure Configuration Baselines and as set forth in the Binding Operational Directive 25-01 Required Configurations website.
- Determine which have been identified as “failures.”
- Follow the steps found in the SCuBA Secure Configuration Baselines to implement the remaining mandatory security policies or identify timelines for required implementations.
- In some cases, ScubaGear may need to be configured with relevant information so that policies successfully pass the evaluation criteria. For example, “break glass” accounts that are exempt from certain policies must be explicitly listed. Additional information is available in the ScubaGear documentation. If an Agency believes there is a condition for which it can receive a deviation for a specific failed control, refer to the user guidance in Requirement #6 for further steps. Re-run ScubaGear again to confirm that the policy failures have been remediated and resubmit the latest SCuBA assessment tool results to CISA as outlined in Requirement #2.
Requirement #4
Implement all future updates to mandatory SCuBA policies in accordance with the timelines set forth in the CISA-managed Binding Operational Directive 25-01 Required Configurations website.
User Guidance: CISA will notify Agencies via email when changes are made to the SCuBA Secure Configuration Baselines. Agencies shall reference the Binding Operational Directive 25-01 Required Configurations website to identify and implement all current Secure Configuration Baselines, mandatory security policies, and timelines for required implementation.
- Follow all above steps and verify that:
- All cloud tenants within the scope of this Directive have been collected and entered on the CyberScope SCuBA Tenant Inventory site.
- The SCuBA assessment tools for in-scope cloud tenants are using one of the SCuBA continuous monitoring solutions or results submitted manually in the CyberScope SCuBA Tenant Inventory site.
- For the mandatory policies identified as “failures”:
- Review the results.
- Follow the steps found in the SCuBA Secure Configuration Baselines to implement the remaining mandatory security policies or identify timelines for required implementations.
Requirement #5
Implement all mandatory SCuBA Secure Configuration Baselines and begin continuous monitoring for new cloud tenants prior to granting an Authorization to Operate (ATO).
User Guidance: When planning to add new cloud instances prior to granting an ATO, Agencies shall reference the Binding Operational Directive 25-01 Required Configurations website to identify all current Secure Configuration Baselines, mandatory security policies and timelines for required implementation.
- For all associated cloud tenants, Agencies must:
- Implement all steps in Requirement #1, except mark the field of ATO to “N” (No) in the tenant inventory in CyberScope. Instructions on how to enter tenant information can be found here.
- Begin steps in Requirement #2.
- Implement all steps in Requirement #3, aside from steps referencing Requirement #2.
- Implement all steps in Requirement #4, aside from steps referencing Requirement #2.
- Once an ATO is granted, mark the ATO field to “Y” (Yes) in the tenant inventory in CyberScope.
- Continue to report as above.
Requirement #6
Agencies shall identify and explain deviations in the output of the SCuBA assessment tools when reported to CISA. For more information regarding this process, review the following and coordinate with CISA via cyberdirectives@mail.cisa.dhs.gov.
User Guidance: The opportunity to document operationally required deviations in the ScubaGear output is satisfied via the ScubaGear configuration file. The config file includes an option allowing users to indicate policies that should be “omitted” or excluded from ScubaGear’s output, indicate the rationale for omission and optionally time-bound the exclusion. (Click here for more information on how to configure omissions in the config file.)
- Operationally required deviations to policies will show up as “Omitted” in the ScubaGear output, along with the accompanying rationale. Omitting policies must only be done if the omissions are approved within an organization's security risk management process. Exercise care when omitting policies because this can inadvertently introduce blind spots in system assessment.
- Agencies that are manually running ScubaGear and need to configure an operationally required deviation should:
- Create a config file documenting the deviations and rationales for deviation. Click here for more information.
- If reporting via CLAW/TALON integration, follow the instructions here for running ScubaGear with a config file and deploy the config file within the environment’s configuration.
- If reporting manually via CyberScope, follow the instructions here for running ScubaGear with a config file.
- As part of the ScubaGear results output, a CSV file is produced to help agencies track non-compliant policies with implementation plans (e.g., Plan of Action and Milestone, or POA&M). The CSV file is a template to track why a policy is non-compliant, what will be done to meet compliance and an anticipated date for compliance, should agencies require it.
- The CyberScope SCuBA Tenant Inventory site, an interactive CyberScope user interface (U/I) available in December 2024. Agencies may begin collecting the inventory in an CyberScope Excel template, currently available via CyberScope.
- Instructions for Automated Reporting Using ScubaConnect (Microsoft 365)
-
Automated Reporting Using ScubaConnect
Requirement #1
Identify all cloud tenants within the scope of this Directive:
1. No later than Friday, February 21, 2025, provide the tenant name (Tenant ID and fully qualified domain name [FQDN]) and the system-owning Agency/component for each tenant, following CISA reporting instructions.
2. Update this inventory in the first quarter annually by following CISA reporting instructions.
NOTE: Annual inventory shall be completed no later than the end of the first quarter in each fiscal year (i.e., December 30, 2025).
- The CyberScope SCuBA Tenant Inventory site, an interactive CyberScope user interface (U/I) available in December 2024. Agencies may begin collecting the inventory in an CyberScope Excel template, currently available via CyberScope.
- Agencies must update their inventory by the end of the first quarter of each fiscal year. The inventory list will be used to help ensure reports for all tenants are being received in a timely manner. Agencies are encouraged to update their inventory immediately when there are changes to tenants. Agencies may complete this requirement manually or with assistance from the output of the ScubaGear tool.
- To access the CyberScope SCuBA Tenant Inventory website, log into an Agency MAX ID account using a registered PIV or CAC card or with a MAX.gov UserID and password.
- To register a MAX ID with CyberScope, register and select “Sign Up” when prompted and select or enter the following:
- Agency: Select the appropriate Agency from the dropdown menu.
- Request Access: Select “Binding Operational Directive 25-01”
-
Work Phone: Enter the user’s work phone number in the format 000-000-0000.
NOTE: CyberScope accounts require approval from Agency specific Department-level POCs. Please coordinate with your component’s top-level Department.
- For users possessing a CyberScope account but not access to the SCuBA Tenant Inventory page, request access by reaching out to the Agency Lead POC or the CyberScope Help Desk (cyberscopehelp@mail.cisa.dhs.gov) to assign the SCuBA BOD Data Entry/Validate and/or Submitter permissions to the CyberScope account.
- To register a MAX ID with CyberScope, register and select “Sign Up” when prompted and select or enter the following:
- With access to the CyberScope SCuBA Tenant Inventory site, select “Add New Tenant.” Then, select or enter the following for all M365 cloud tenants within the scope of this Directive:
- Bureau/Sub-Component: Select the bureau or sub-component that the tenant is operated for. (Each user is already assigned to an Agency; therefore, CyberScope is aware of this context, and all tenants added by a user will be assigned to the Agency. The Bureau/Sub-Component list will be limited to the user’s Agency. Example: If a user’s component was CISA under the Department of Homeland Security (DHS), the user’s Agency is DHS; the bureau or sub-component would be CISA. If the tenant was operated by DHS HQ, no bureau or sub-component would be selected.)
- If no sub-component, insert Agency name.
- Product: Select M365.
- Service Plan: For M365, select either Commercial, GCC, or GCC High.
- Tenant ID: Enter the globally unique identifier (GUID) for the tenant.
- Microsoft Entra admin center:
- Sign in to the Microsoft Entra admin center as at least a Global Reader.
- Browse to Identity > Overview > Properties.
- Scroll down to the Tenant ID section to find the tenant ID in the box.
- Azure Portal
- Sign in to the Azure portal.
- Browse to Microsoft Entra ID > Properties.
- Scroll down to the Tenant ID section to find the tenant ID listed.
- Other: PowerShell, Azure, or M365 command line interface (CLI)
- Follow the commands listed in How to find your tenant ID - Microsoft Entra | Microsoft Learn
- Microsoft Entra admin center:
- Tenant FQDN: Enter the FQDN for the tenant (e.g., cisa.onmicrosoft.com).
- Microsoft Entra admin center:
- Sign in to the Microsoft Entra admin center as at least a Global Reader.
- Browse to Identity > Overview
- Scroll down to the Primary Domain section to find the Tenant FQDN listed.
- Microsoft Entra admin center:
- In Scope: The default is “Y” (Yes) when entering a new tenant. If a tenant falls out of scope or an Agency is pre-emptively listing a tenant they know will soon be within the scope of the BOD, then change this value to “N” (No). Subsequently, CISA will know not to expect results from the tenant.
- When “N” (No) is selected, data for the associated tenant will be shown on a normal Agency dashboard, but will not be shown on the BOD 25-01 CDM dashboard or used for compliance.
- This option is included to allow Agencies flexibility in maintaining current inventory data:
- Agencies can use the CDM infrastructure to track their cloud tenants and view their inventories through their own CDM dashboards.
- Agencies can prepopulate inventories as they bring new tenants on-board and prepare for additional tenants entering the scope of the Directive.
- Agencies can adjust their inventory through a single field without having to delete and re-add data. For example, if a tenant is taken offline for a period of time but will re-enter production again at a later date.
- ATO: Select “Y” (Yes) if the tenant has an active Authorization to Operate (ATO).
- Bureau/Sub-Component: Select the bureau or sub-component that the tenant is operated for. (Each user is already assigned to an Agency; therefore, CyberScope is aware of this context, and all tenants added by a user will be assigned to the Agency. The Bureau/Sub-Component list will be limited to the user’s Agency. Example: If a user’s component was CISA under the Department of Homeland Security (DHS), the user’s Agency is DHS; the bureau or sub-component would be CISA. If the tenant was operated by DHS HQ, no bureau or sub-component would be selected.)
- Agencies can run ScubaGear on each M365 tenant to help fill out the CyberScope SCuBA Tenant Inventory fields. See Requirement #2 for information on running ScubaGear.
- To install and run ScubaGear, refer to the ScubaGear GitHub README. The README contains instructions to install ScubaGear from PowerShell Gallery. Find information on the ScubaGear reports in the ScubaGear documentation on GitHub.
- Note: CISA recognizes the varied internal Agency processes that must be followed to authorize software use on Agency networks. Agencies should initiate those processes as needed for ScubaGear and its dependencies.
Requirement #2
For Automated Reporting Selection: Deploy all SCuBA assessment tools for in-scope cloud tenants no later than Friday, April 25, 2025 and begin continuous reporting on the requirements of this Directive through integrating the tool results feeds with CISA’s continuous monitoring solution to enable automated reporting.
User Guidance: If your Agency has selected the fully automated reporting method, your Agency will achieve this requirement by running ScubaGear on all in-scope tenants, managed by CISA, that will enable automated ScubaGear scanning and reporting compliance.
- First, install and configure the ScubaGear tool to run assessments on all in- scope tenants:

- Within the ScubaGear Configuration File, Agencies should insert values for their Department-level Agency name in the “OrgName” of the config file and, if applicable, they should enter the sub-component, bureau, or subagency name in the “OrgUnitName” of the config file.
- Note: The “OrgName” should be the top-level Agency acronym as defined under CISA’s Federal Civilian Executive Branch Agency List. The “OrgUnitName” should be the next organization acronym one level down from the top level. Example below and link to a sample config file:
- E.g., OrgName: “DHS”
- E.g., OrgUnitName: “CISA” (if applicable)
- Note: If your bureau has a separate CDM deployment, you should have that bureau reported as OrgName. This does not apply for most customers. If OrgUnitName is not applicable, then enter OrgUnitName: “”
- Note: The “OrgName” should be the top-level Agency acronym as defined under CISA’s Federal Civilian Executive Branch Agency List. The “OrgUnitName” should be the next organization acronym one level down from the top level. Example below and link to a sample config file:
- Agencies may refer to the Binding Operational Directive 25-01 Required Configurations website for links and additional guidance.
- Note: CISA recognizes that using software on agency networks may require following internal agency authorization processes. Agencies should initiate those processes as needed for ScubaGear and its dependencies.
- For each tenant listed as “In Scope,” the user will need to provide the results from the latest version of the SCuBA assessment tool to CISA.
- ScubaConnect runs from a CISA environment as though the application was native to an agency’s tenant.
- Agencies will grant access to their tenant to a CISA owned and operated multi-tenant application, and results will automatically be provided back to the agency through the CDM Dashboard.
- Beyond initial configuration, CISA will manage reporting compliance via ScubaConnect without additional workload requirements on agencies.
- Agencies complete the following steps to complete integration with ScubaConnect:
- Email the SCuBA Team at scuba@mail.cisa.dhs.gov.
- A tenant admin with sufficient privileges will need to be able to approve the consent link and ensure permissions are correctly set.
- The agency will need to upload their ScubaGear configuration file to CyberScope for the appropriate tenant.
Requirement #3
Implement all mandatory SCuBA policies effective as of this Directive’s issuance, as set forth in the CISA-managed Binding Operational Directive 25-01 Required Configurations website no later than Friday, June 20, 2025. These mandatory SCuBA policies are provided on the Required Configurations website and correspond to the mandatory policies referenced within the SCuBA Secure Configuration Baselines.
User Guidance: When implementing mandatory policies to all cloud instances covered by this BOD, Agencies shall reference the Binding Operational Directive 25-01 Required Configurations website.
- Follow all steps identified in Requirements #1 and #2, verifying that:
- All cloud tenants within the scope of this Directive have been collected and entered on the CyberScope SCuBA Tenant Inventory site.
- For the mandatory policies identified as “failures,” follow the next steps below:
- Go to the CDM dashboard to find the mandatory policies identified as “failures.”
- Review and follow the steps found in the SCuBA Secure Configuration Baselines to implement the remaining mandatory security policies or identify timelines for required implementations.
- In some cases, ScubaGear may need to be configured with relevant information so that policies successfully pass the evaluation criteria. For example, “break glass” accounts that are exempt from certain policies must be explicitly listed. Additional information is available in the ScubaGear documentation. If an Agency believes there is a condition for which it can receive a deviation for a specific failed control, refer to the user guidance in Requirement #6 for further steps. Re-run ScubaGear again to confirm that the policy failures have been remediated and resubmit the latest SCuBA assessment tool results to CISA as outlined in Requirement #2.
Requirement #4
Implement all future updates to mandatory SCuBA policies in accordance with the timelines set forth in the CISA-managed Binding Operational Directive 25-01 Required Configurations website.
User Guidance: CISA will notify Agencies via email when changes are made to the SCuBA Secure Configuration Baselines. Agencies shall reference the Binding Operational Directive 25-01 Required Configurations website to identify and implement all current Secure Configuration Baselines, mandatory security policies, and timelines for required implementation.
- Follow all above steps and verify that:
- All cloud tenants within the scope of this Directive have been collected and entered on the CyberScope SCuBA Tenant Inventory site.
- The SCuBA assessment tools for in-scope cloud tenants are using the SCuBA continuous monitoring solutions.
- For the mandatory policies identified as “failures”:
- Review the results.
- Follow the steps found in the SCuBA Secure Configuration Baselines to implement the remaining mandatory security policies or identify timelines for required implementations.
Requirement #5
Implement all mandatory SCuBA Secure Configuration Baselines and begin continuous monitoring for new cloud tenants prior to granting an Authorization to Operate (ATO).
User Guidance: When planning to add new cloud instances prior to granting an ATO, Agencies shall reference the Binding Operational Directive 25-01 Required Configurations website to identify all current Secure Configuration Baselines, mandatory security policies and timelines for required implementation.
- For all associated cloud tenants, Agencies must:
- Implement all steps in Requirement #1, except mark the field of ATO to “N” (No) in the tenant inventory in CyberScope. Instructions on how to enter tenant information can be found here.
- Begin steps in Requirement #2.
- Implement all steps in Requirement #3, aside from steps referencing Requirement #2.
- Implement all steps in Requirement #4, aside from steps referencing Requirement #2.
- Once an ATO is granted, mark the ATO field to “Y” (Yes) in the tenant inventory in CyberScope.
- Continue to report as above.
Requirement #6
Agencies shall identify and explain deviations in the output of the SCuBA assessment tools when reported to CISA. For more information regarding this process, review the following and coordinate with CISA via cyberdirectives@mail.cisa.dhs.gov.
User Guidance: The opportunity to document operationally required deviations in the ScubaGear output is satisfied via the ScubaGear configuration file. The config file includes an option allowing users to indicate policies that should be “omitted” or excluded from ScubaGear’s output, indicate the rationale for omission and optionally time-bound the exclusion. (Click here for more information on how to configure omissions in the config file.)
- Operationally required deviations to policies will show up as “Omitted” in the ScubaGear output, along with the accompanying rationale. Omitting policies must only be done if the omissions are approved within an organization's security risk management process. Exercise care when omitting policies because this can inadvertently introduce blind spots in system assessment.
- Agencies that have integrated with ScubaConnect should:
- Modify their config file documenting the deviations and rationales for deviation. Click here for more information.
- Manually upload the config file via CyberScope if they are using ScubaConnect hosted by CISA or follow the procedures for a parent organization has setup for providing an updated config file for a self-hosted ScubaConnect option.
- Follow the instructions here for running ScubaGear with a config file.
- The CyberScope SCuBA Tenant Inventory site, an interactive CyberScope user interface (U/I) available in December 2024. Agencies may begin collecting the inventory in an CyberScope Excel template, currently available via CyberScope.
- Instructions for Agency-Hosted (Semi-Automated) Reporting (Microsoft 365)
-
Agency-Hosted (Semi-Automated) Reporting
Requirement #1
Identify all cloud tenants within the scope of this Directive:
1. No later than Friday, February 21, 2025, provide the tenant name (Tenant ID and fully qualified domain name [FQDN]) and the system-owning Agency/component for each tenant, following CISA reporting instructions.
2. Update this inventory in the first quarter annually by following CISA reporting instructions.
- The CyberScope SCuBA Tenant Inventory site, an interactive CyberScope user interface (U/I) available in December 2024. Agencies may begin collecting the inventory in an CyberScope Excel template, currently available via CyberScope.
- Agencies must update their inventory by the end of the first quarter of each fiscal year. The inventory list will be used to help ensure reports for all tenants are being received in a timely manner. Agencies are encouraged to update their inventory immediately when there are changes to tenants. Agencies may complete this requirement manually or with assistance from the output of the ScubaGear tool.
- To access the CyberScope SCuBA Tenant Inventory website, log into an Agency MAX ID account using a registered PIV or CAC card or with a MAX.gov UserID and password.
- To register a MAX ID with CyberScope, register and select “Sign Up” when prompted and select or enter the following:
- Agency: Select the appropriate Agency from the dropdown menu.
- Request Access: Select “Binding Operational Directive 25-01”
-
Work Phone: Enter the user’s work phone number in the format 000-000-0000.
NOTE: CyberScope accounts require approval from Agency specific Department-level POCs. Please coordinate with your component’s top-level Department.
- For users possessing a CyberScope account but not access to the SCuBA Tenant Inventory page, request access by reaching out to the Agency Lead POC or the CyberScope Help Desk (cyberscopehelp@mail.cisa.dhs.gov) to assign the SCuBA BOD Data Entry/Validate and/or Submitter permissions to the CyberScope account.
- To register a MAX ID with CyberScope, register and select “Sign Up” when prompted and select or enter the following:
- With access to the CyberScope SCuBA Tenant Inventory site, select “Add New Tenant.” Then, select or enter the following for all M365 cloud tenants within the scope of this Directive:
- Bureau/Sub-Component: Select the bureau or sub-component that the tenant is operated for. (Each user is already assigned to an Agency; therefore, CyberScope is aware of this context, and all tenants added by a user will be assigned to the Agency. The Bureau/Sub-Component list will be limited to the user’s Agency. Example: If a user’s component was CISA under the Department of Homeland Security (DHS), the user’s Agency is DHS; the bureau or sub-component would be CISA. If the tenant was operated by DHS HQ, no bureau or sub-component would be selected.)
- If no sub-component, insert Agency name.
- Product: Select M365.
- Service Plan: For M365, select either Commercial, GCC, or GCC High.
- Tenant ID: Enter the globally unique identifier (GUID) for the tenant.
- Microsoft Entra admin center:
- Sign in to the Microsoft Entra admin center as at least a Global Reader.
- Browse to Identity > Overview > Properties.
- Scroll down to the Tenant ID section to find the tenant ID in the box.
- Azure Portal
- Sign in to the Azure portal.
- Browse to Microsoft Entra ID > Properties.
- Scroll down to the Tenant ID section to find the tenant ID listed.
- Other: PowerShell, Azure, or M365 command line interface (CLI)
- Follow the commands listed in How to find your tenant ID - Microsoft Entra | Microsoft Learn
- Microsoft Entra admin center:
- Tenant FQDN: Enter the FQDN for the tenant (e.g., cisa.onmicrosoft.com).
- Microsoft Entra admin center:
- Sign in to the Microsoft Entra admin center as at least a Global Reader.
- Browse to Identity > Overview
- Scroll down to the Primary Domain section to find the Tenant FQDN listed.
- Microsoft Entra admin center:
- In Scope: The default is “Y” (Yes) when entering a new tenant. If a tenant falls out of scope or an Agency is pre-emptively listing a tenant they know will soon be within the scope of the BOD, then change this value to “N” (No). Subsequently, CISA will know not to expect results from the tenant.
- When “N” (No) is selected, data for the associated tenant will be shown on a normal Agency dashboard, but will not be shown on the BOD 25-01 CDM dashboard or used for compliance.
- This option is included to allow Agencies flexibility in maintaining current inventory data:
- Agencies can use the CDM infrastructure to track their cloud tenants and view their inventories through their own CDM dashboards.
- Agencies can prepopulate inventories as they bring new tenants on-board and prepare for additional tenants entering the scope of the Directive.
- Agencies can adjust their inventory through a single field without having to delete and re-add data. For example, if a tenant is taken offline for a period of time but will re-enter production again at a later date.
- ATO: Select “Y” (Yes) if the tenant has an active Authorization to Operate (ATO).
- Bureau/Sub-Component: Select the bureau or sub-component that the tenant is operated for. (Each user is already assigned to an Agency; therefore, CyberScope is aware of this context, and all tenants added by a user will be assigned to the Agency. The Bureau/Sub-Component list will be limited to the user’s Agency. Example: If a user’s component was CISA under the Department of Homeland Security (DHS), the user’s Agency is DHS; the bureau or sub-component would be CISA. If the tenant was operated by DHS HQ, no bureau or sub-component would be selected.)
- Agencies can run ScubaGear on each M365 tenant to help fill out the CyberScope SCuBA Tenant Inventory fields. See Requirement #2 for information on running ScubaGear.
- To install and run ScubaGear, refer to the ScubaGear GitHub README. The README contains instructions to install ScubaGear from PowerShell Gallery. Find information on the ScubaGear reports in the ScubaGear documentation on GitHub.
- Note: CISA recognizes the varied internal Agency processes that must be followed to authorize software use on Agency networks. Agencies should initiate those processes as needed for ScubaGear and its dependencies.
Requirement #2
For Agency-Hosted Reporting Selection: Deploy all SCuBA assessment tools for in-scope cloud tenants no later than Friday, April 25, 2025 and begin continuous reporting on the requirements of this Directive through one of the following methods:
1. Integrate the tool results feeds with your Agency’s continuous monitoring solution to enable automated reporting
AND
- Note: Department sub-components should coordinate with their top-level Departments. Manual reporting in CyberScope is typically submitted by Department-level POCs.
User Guidance: To achieve compliance, agencies will run ScubaGear on all in-scope tenants. This section provides an overview of how Agencies can automate reporting to CISA via integration with CLAW / TALON using Agency-hosted resources.
- The first includes automated reporting options, including one managed by CISA and are “set-and-forget” options that will enable automated ScubaGear scanning and reporting compliance.
- The second is manual configuration of the assessment tool with a quarterly reporting obligation of Agency results to CISA.
Prior to selection, the following items are required to ensure proper configuration of the ScubaGear tool to run assessments:

- Within the ScubaGear Configuration File, Agencies should insert values for their Department-level Agency name in the “OrgName” of the config file and, if applicable, they should enter the sub-component, bureau, or subagency name in the “OrgUnitName” of the config file.
- Note: The “OrgName” should be the top-level Agency acronym as defined under CISA’s Federal Civilian Executive Branch Agency List. The “OrgUnitName” should be the next organization acronym one level down from the top level. Example below and link to a sample config file:
- E.g., OrgName: “DHS”
- E.g., OrgUnitName: “CISA” (if applicable)
- Note: If your bureau has a separate CDM deployment, you should have that bureau reported as OrgName. This does not apply for most customers. If OrgUnitName is not applicable, then enter OrgUnitName: “”
- Note: The “OrgName” should be the top-level Agency acronym as defined under CISA’s Federal Civilian Executive Branch Agency List. The “OrgUnitName” should be the next organization acronym one level down from the top level. Example below and link to a sample config file:
- Agencies may refer to the Binding Operational Directive 25-01 Required Configurations website for links and additional guidance.
- Note: CISA recognizes the varied internal Agency processes that must be followed to authorize software use on Agency networks. Agencies should initiate those processes as needed for ScubaGear and its dependencies.
- Agencies opting to self-host ScubaConnect can set up the ability to automate running ScubaGear and submit results to CISA. This option also allows Agencies to keep a copy of their results file locally. Additionally, this option allows for a parent Agency to set up and run ScubaGear for all of their components. This option uses Agency resources to run ScubaConnect and ScubaGear. Agencies may configure ScubaGear to run and report results as often as they want, with a minimum of once per quarter. This can be done by:
- Downloading ScubaConnect from CISA’s GitHub.
- Contacting CISA to set up integration of the environment running the self-hosted ScubaConnect with a CLAW/TALON by emailing the SCuBA Team at scuba@mail.cisa.dhs.gov.
- Keeping up-to-date with new ScubaGear containers to ensure the latest version of ScubaGear is being run.
- Ensuring there is a properly configured YAML file for each tenant that will be scanned.
- Agency runs ScubaGear and automates reporting of results to CISA via integration with CLAW/TALON using Agency-hosted resources.
- In this option, Agencies run regular automated ScubaGear scans hosted in an Agency cloud environment and provide the results to CISA through the CLAW Azure TALON. This is a more advanced option for Agencies that wish to automate ScubaGear reporting and will require integration and development work on the Agency side.
- After each ScubaGear scan is run within the environment, the outputs should be sent to a CLAW Azure TALON. Do not change the filename of the results output. The file name has this pattern: ScubaResults_UUID.json, where the UUID is an 18-digit string of numbers and characters.
- Agencies are responsible for ensuring that they are running the latest version of ScubaGear.
- Agencies may configure ScubaGear to run and report results as often as they want, with a minimum of once per quarter.
- For agencies looking for further guidance to pursue this option, please contact CISA at scuba@mail.cisa.dhs.gov to discuss integration requirements in more detail.
- Agency manually runs ScubaGear and reports the results to CISA by manually uploading them to CyberScope.
- In this option, agencies manually upload ScubaGear assessment results to CISA quarterly through CyberScope. Results will be updated in the CDM dashboard upon receipt by CISA. If desired, agencies may update results in CyberScope more frequently. For agencies manually reporting results, follow the steps in Requirement #1 to ensure all cloud tenants within the scope of this Directive have their required information collected and listed via CyberScope.
- Agencies must configure and run ScubaGear for all in-scope tenants.
- Refer to the ScubaGear GitHub README, which contains instructions to install ScubaGear from PowerShell Gallery.
- After running the ScubaGear tool for each in-scope tenant, log in to CyberScope and select the “v” symbol at the end of each row to open the submission section for the tenant.
- For Submission Type, select from the dropdown menu “Scan Results.”
- Select and submit the SCuBA assessment tool results by dragging and dropping the file or selecting browse and selecting the file. For the “Scan Results” requirement, the file type is limited to:
- .json: grab and drop or select via browse the ScubaResults .json file in the output directory folder. The ScubaResults file will include about 18 characters that are part of the UUID (unique identifier that is generated for each report; the full report unique identifier is available in the .json file) prior to the .json file extension. Do not alter the file name produced by the ScubaGear tool before submitting results to CyberScope.
- Agencies will then upload the resulting output via the BOD 25-01 CyberScope page.
- Agencies must configure and run ScubaGear for all in-scope tenants.
- In this option, agencies manually upload ScubaGear assessment results to CISA quarterly through CyberScope. Results will be updated in the CDM dashboard upon receipt by CISA. If desired, agencies may update results in CyberScope more frequently. For agencies manually reporting results, follow the steps in Requirement #1 to ensure all cloud tenants within the scope of this Directive have their required information collected and listed via CyberScope.
Requirement #3
Implement all mandatory SCuBA policies effective as of this Directive’s issuance, as set forth in the CISA-managed Binding Operational Directive 25-01 Required Configurations website no later than Friday, June 20, 2025. These mandatory SCuBA policies are provided on the Required Configurations website and correspond to the mandatory policies referenced within the SCuBA Secure Configuration Baselines.
User Guidance: When implementing mandatory policies to all cloud instances covered by this BOD, Agencies shall reference the Binding Operational Directive 25-01 Required Configurations website.
- Follow all steps identified in Requirements #1 and #2, verifying that:
- All cloud tenants within the scope of this Directive have been collected and entered on the CyberScope SCuBA Tenant Inventory site.
- SCuBA assessment tools for in-scope cloud tenants have been enrolled in the SCuBA continuous reporting solution or results submitted manually in the CyberScope SCuBA Tenant Inventory site.
- All cloud tenants within the scope of this Directive have been collected and entered on the CyberScope SCuBA Tenant Inventory site.
- For the mandatory policies identified as “failures,” follow the next steps below:
- Continuous Monitoring Solution (Use for agencies and tenants that are using one of the continuous monitoring solutions.) Do the following:
- Go to the CDM dashboard to find the mandatory policies identified as “failures.”
- Review and follow the steps found in the SCuBA Secure Configuration Baselines to implement the remaining mandatory security policies or identify timelines for required implementations.
- Manually Reporting (Use for agencies and tenants that submitted the SCuBA assessment tool results manually.) Do the following:
- Open the file name BaselineReports.html to view the SCuBA M365 Secure Baseline Conformance Report.
- Review all mandatory policies referenced within the SCuBA Secure Configuration Baselines and as set forth in the Binding Operational Directive 25-01 Required Configurations website.
- Determine which have been identified as “failures.”
- Follow the steps found in the SCuBA Secure Configuration Baselines to implement the remaining mandatory security policies or identify timelines for required implementations.
- In some cases, ScubaGear may need to be configured with relevant information so that policies successfully pass the evaluation criteria. For example, “break glass” accounts that are exempt from certain policies must be explicitly listed. Additional information is available in the ScubaGear documentation. If an Agency believes there is a condition for which it can receive a deviation for a specific failed control, refer to the user guidance in Requirement #6 for further steps. Re-run ScubaGear again to confirm that the policy failures have been remediated and resubmit the latest SCuBA assessment tool results to CISA as outlined in Requirement #2.
- Continuous Monitoring Solution (Use for agencies and tenants that are using one of the continuous monitoring solutions.) Do the following:
Requirement #4
Implement all future updates to mandatory SCuBA policies in accordance with the timelines set forth in the CISA-managed Binding Operational Directive 25-01 Required Configurations website.
User Guidance: CISA will notify Agencies via email when changes are made to the SCuBA Secure Configuration Baselines. Agencies shall reference the Binding Operational Directive 25-01 Required Configurations website to identify and implement all current Secure Configuration Baselines, mandatory security policies, and timelines for required implementation.
- Follow all above steps and verify that:
- All cloud tenants within the scope of this Directive have been collected and entered on the CyberScope SCuBA Tenant Inventory site.
- The SCuBA assessment tools for in-scope cloud tenants are using one of the SCuBA continuous monitoring solutions or results submitted manually in the CyberScope SCuBA Tenant Inventory site.
- For the mandatory policies identified as “failures”:
- Review the results.
- Follow the steps found in the SCuBA Secure Configuration Baselines to implement the remaining mandatory security policies or identify timelines for required implementations.
Requirement #5
Implement all mandatory SCuBA Secure Configuration Baselines and begin continuous monitoring for new cloud tenants prior to granting an Authorization to Operate (ATO).
User Guidance: When planning to add new cloud instances prior to granting an ATO, Agencies shall reference the Binding Operational Directive 25-01 Required Configurations website to identify all current Secure Configuration Baselines, mandatory security policies and timelines for required implementation.
- For all associated cloud tenants, Agencies must:
- Implement all steps in Requirement #1, except mark the field of ATO to “N” (No) in the tenant inventory in CyberScope. Instructions on how to enter tenant information can be found here.
- Begin steps in Requirement #2.
- Implement all steps in Requirement #3, aside from steps referencing Requirement #2.
- Implement all steps in Requirement #4, aside from steps referencing Requirement #2.
- Once an ATO is granted, mark the ATO field to “Y” (Yes) in the tenant inventory in CyberScope.
- Continue to report as above.
Requirement #6
Agencies shall identify and explain deviations in the output of the SCuBA assessment tools when reported to CISA. For more information regarding this process, review the following and coordinate with CISA via cyberdirectives@mail.cisa.dhs.gov.
User Guidance: The opportunity to document operationally required deviations in the ScubaGear output is satisfied via the ScubaGear configuration file. The config file includes an option allowing users to indicate policies that should be “omitted” or excluded from ScubaGear’s output, indicate the rationale for omission and optionally time-bound the exclusion. (Click here for more information on how to configure omissions in the config file.)
- Operationally required deviations to policies will show up as “Omitted” in the ScubaGear output, along with the accompanying rationale. Omitting policies must only be done if the omissions are approved within an organization's security risk management process. Exercise care when omitting policies because this can inadvertently introduce blind spots in system assessment.
- Agencies that have integrated with ScubaConnect should:
- Modify their config file documenting the deviations and rationales for deviation. Click here for more information.
- Manually upload the config file via CyberScope if they are using ScubaConnect hosted by CISA or follow the procedures for a parent organization has setup for providing an updated config file for a self-hosted ScubaConnect option.
- Follow the instructions here for running ScubaGear with a config file.
- Agencies that are manually running ScubaGear and need to configure an operationally required deviation should:
- Create a config file documenting the deviations and rationales for deviation. Click here for more information.
- If reporting via CLAW/TALON integration, follow the instructions here for running ScubaGear with a config file and deploy the config file within the environment’s configuration.
- If reporting manually via CyberScope, follow the instructions here for running ScubaGear with a config file.
- As part of the ScubaGear results output, a CSV file is produced to help agencies track non-compliant policies with implementation plans (e.g., Plan of Action and Milestone, or POA&M). The CSV file is a template to track why a policy is non-compliant, what will be done to meet compliance and an anticipated date for compliance, should agencies require it.
- The CyberScope SCuBA Tenant Inventory site, an interactive CyberScope user interface (U/I) available in December 2024. Agencies may begin collecting the inventory in an CyberScope Excel template, currently available via CyberScope.
SCuBA Policies and Assessment Tool Updates
Instructions on how to sign up for GovDelivery can be found on the CISA website “Subscribe to Updates from CISA.”
- Click the “Subscribe” button under “Subscribe to Email Updates.”
- A prompt will inform the user that they are leaving an official U.S. Government website, click “OK.” Follow the prompts to create a user profile.
- Under “Subscription Topics” select BOD 25-01: Implementing Secure Cloud Practices for SCuBA BOD-specific policy updates and tool changes.
- Once the desired selections are made, click “Submit.”
Templates
CyberScope User Interface Inventory Tracker
CyberScope Inventory Excel Tracker
Frequently Asked Questions
General Questions
Q: I have questions about this BOD. Whom do I talk to?
A:
- For general information, assistance, and questions about reporting and compliance, visit Cybersecurity Directives | CISA or contact CyberDirectives@mail.cisa.dhs.gov.
- For questions about the SCuBA program, Secure Configuration Baselines, the assessment and tools, managing inventory or uploading SCuBA files to CyberScope, integrating SCuBA results to CLAW Azure TALONs, and/or viewing SCuBA results in CDM, contact the SCuBA team at scuba@mail.cisa.dhs.gov.
Q: For which vendors are the SCuBA Secure Configuration Baselines currently operational?
A: CISA is actively constructing a robust framework aimed at developing SCuBA’s Secure Configuration Baselines for various SaaS products, aligning closely with the Federal Risk and Authorization Management Program, or FedRAMP. CISA has released finalized Secure Configuration Baselines for M365 (which is in-scope for the BOD at issuance) and draft Secure Configuration Baselines for Google Workspace, or GWS (which are anticipated to enter scope in the second quarter of fiscal year 2025). CISA will continue its collaboration with agencies, organizations, and cloud service providers to keep these baselines up-to-date to reflect the latest security standards and threats. This ongoing partnership and proactive approach will help maintain a resilient, secure, and adaptable digital environment.
Q: Is CISA developing SCuBA Secure Configuration Baselines for other vendors?
A: Currently, only the M365 baseline is finalized and in scope for this Directive. In the future, CISA may release additional SCuBA Secure Configuration Baselines for other cloud products.
Q: What type of licenses are needed for compliance with the policy requirements of the Secure Configuration Baselines?
A: For M365, license assumptions are listed in the licensing requirements. Some policies require additional licenses, either from Microsoft or a third-party service that offers equivalent protections, as noted in the "License Requirements" sections of the individual controls. The specific service used to meet the requirement for policies that require additional licensing is left up to Agency discretion.
Q: What do I do if my Agency has not purchased the license tiers needed for compliance with the policy requirements of the Secure Configuration Baselines?
A: Purchasing additional licensing is not a requirement of the BOD. Agencies may use third-party capabilities that provide equivalent protections, and more details can be found within the baselines. Agencies may also indicate a deviation in their configuration file and include the reason for the deviation.
Q: How do I download the assessment tool?
A: ScubaGear is available for download on CISA’s GitHub. Installation instructions can also be found on its GitHub page in the README file. For simplicity, ScubaGear can be installed directly through PowerShell Gallery. Agencies can also download signed releases from GitHub for packaging and distribution through Agency enterprise software management infrastructure.
Q: What does each baseline policy contain?
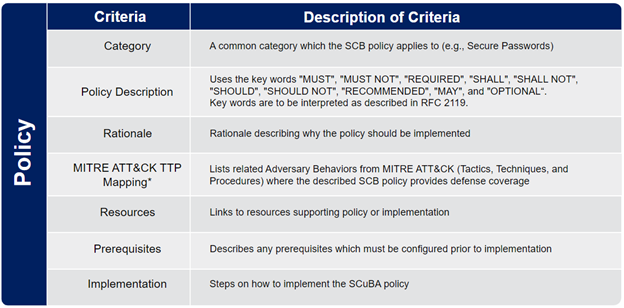
A: SCuBA Secure Configuration Baselines are organized topically by policy groups, such as Risk Based Policies, Strong Authentication and a Secure Registration Process, or Application Registration and Consent, etc. To help users better understand each individual baseline policy, CISA includes the following information:
Q: What do the different colors (green, yellow, red, and gray) in my SCuBA tool report represent?
A: Once the tool has generated the report, it will show all baselines with indications of “passed,” “warning,” “failed,” “omitted,” or “manual checks needed.” Green indicates the controls that passed or are compliant with the security baseline statements. Red indicates that required baselines statement controls are not met, i.e., “shall” statements. Yellow indicates that recommended baselines statement controls are not met, i.e., “should” statements. Gray indicates the controls that ScubaGear is not able to evaluate using the Application Programming Interfaces, or APIs provided by the cloud service provider. See below for an example:
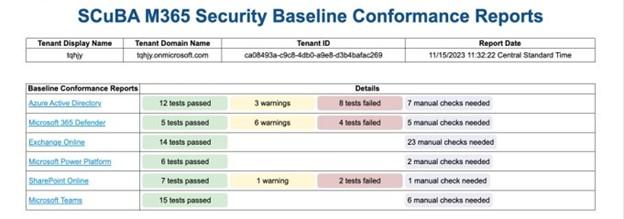
Q: Our Agency implements Zero Trust Architecture. Does this Directive still apply to us?
A: This Directive’s requirements complement and support zero trust (ZT) implementation principles. Agencies should complete the required actions outlined in this Directive in parallel to adopting ZT principles, in accordance with CISA’s ZT Maturity Model.
Q: Will CISA make the SCuBA assessment data available to my Agency?
A: All results received by CISA through either the automated reporting tool (ScubaConnect) or via CyberScope will be made available to both the Federal and Agency Dashboards within CDM. This enables Agencies to track Directive implementation progress and ongoing compliance for all in scope tenants across the Agency.
ScubaGear (M365) Questions
Q: What is ScubaGear?
A: ScubaGear is a tool for automatically assessing whether a given tenant properly implements the Secure Configuration Baselines requirements for M365. ScubaGear assesses the Secure Configuration Baselines for a specific M365 tenant, supporting products like Azure Active Directory/Entra ID, Exchange Online, Defender for Office 365, SharePoint and OneDrive Online, Microsoft Teams, and Power Platform.
Q: What permissions on my tenant are required for my Agency to run ScubaGear?
A: ScubaGear utilizes two distinct permissions sets for authentication: interactive authentication and non-interactive authentication. Each has separate permission requirements to accommodate different security and operational needs. Interactive authentication allows users to directly sign in to ScubaGear, whereas non-interactive authentication requires an Entra ID service principal to sign into the tool. For more information and to keep up-to-date with permission requirement changes, please refer to the interactive permissions and non-interactive permissions GitHub pages.
Q: What are the requirements for running ScubaGear in my environment?
A: ScubaGear has a base license assumption of M365 G3 or E3; however, some controls require additional add-on licensing (e.g., Entra ID P2). ScubaGear must be run on a PowerShell 5.1 terminal (the default version that ships with Windows) in a Microsoft Windows environment with an identity that possesses the required M365 permissions. ScubaGear also requires several dependencies. Normally, these dependencies are automatically installed during setup, but in some cases, Agencies may need to manually package ScubaGear and its dependencies for deployment within their environment. If agencies use ScubaConnect, there is no requirement to run ScubaGear locally within the Agency environment.
Q: Where is the best place to view the Secure Configuration Baselines for M365?
A: The Binding Operational Directive 25-01 Required Configurations website is the best way to see all mandatory M365 configurations within the scope of this Directive. Additionally, the Secure Configuration Baselines are available for download by policy group on the CISA.gov SCuBA homepage. They can also be found on the ScubaGear GitHub page in the “baselines” folder.
Resources
- SCuBA Homepage
- SCuBA YouTube Channel
- Slack Channel Registration
- NIST Digital Identity Guidelines
- NIST Cybersecurity Log Management Planning Guide
- CommunityConnect (OMB MAX; PIV/CAC Required)
- Serves as a comprehensive resource for all things SCuBA, offering users easy access to key information and tools. Contains a wide range of training materials, including instructional videos, workshop recordings, demos and detailed slide decks, all designed to keep users informed and equipped with additional knowledge to utilize these assessment tools.
- BOD 25-01 Questions and Answers (OMB MAX; PIV/CAC Required)
- Updated Q&A spreadsheet from past BOD 25-01 webinars and office hours that provides answers to frequently asked questions.
Training
Glossary
| Term | Definition |
|---|---|
| API | Application Programming Interface |
| ATO | Authorization to Operate |
| BOD | Binding Operational Directive |
| CDM | Continuous Diagnostics and Mitigation |
| CISA | Cybersecurity and Infrastructure Security Agency |
| CLAW | Comprehensive Log Aggregation Warehouse |
| CLI | Command Line Interface |
| CSP | Cloud Service Provider |
| CSV | Comma-Separated Values |
| DHS | Department of Homeland Security |
| FCEB | Federal Civilian Executive Branch |
| FedRAMP | Federal Risk and Authorization Management Program |
| FQDN | Fully Qualified Domain Name |
| GCC | Government Community Cloud |
| GUID/UUID | Globally Unique Identifier/Universally Unique Identifier |
| GWS | Google Workspace |
| IaaS | Infrastructure as a Service |
| JSON | JavaScript Object Notation |
| M365 | Microsoft 365 |
| NIST | National Institute of Standards and Technology |
| OMB | Office of Management and Budget |
| PaaS | Platform as a Service |
| PIV/CAC | Personal Identity Verification card/Common Access Card |
| POA&M | Plan of Action and Milestones |
| POC | Point of Contact |
| PSGallery | PowerShell Gallery |
| SaaS | Software as a Service |
| SCB | Secure Configuration Baseline |
| SCuBA | Secure Cloud Business Applications |
| TALON | Transfer at Location Optimized Node |
| U/I | User Interface |
| ZT | Zero Trust |
Definitions
| App ID | A unique identifier for applications in Entra ID, such as ScubaConnect. This identifier is used when a tenant admin consents (provides permissions to) the ScubaConnect application. |
| Deviation | A difference between a tenant environment and the ScubaGear Secure Configuration Baseline. Deviations normally result in a failed control when evaluated by ScubaGear. Those deemed operationally required can be declared in the configuration file, excluding the corresponding control from evaluation. |
| Fully Qualified Domain Name (FQDN) | The complete URL for a website or server, which includes the host name, domain name, and top-level domain. It is more precise than using an IP address or a partially qualified domain name. |
| Omit Policies | In some cases, it may be appropriate to omit specific policies from ScubaGear evaluation. Such policies will appear as “omitted” and be colored gray in the HTML report. Omitting policies must only be done if the omissions are approved within an organization’s security risk management process. |
| Operational and/or Production Tenants | A Cloud Service Provider environment primarily used by the government to conduct official government business, whether operated by the government or a contractor. |
| OrgName | The top-level Agency acronym as defined under CISA’s Federal Civilian Executive Branch Agency List. For example, “DHS” is the OrgName for the Department of Homeland Security. This is to be inserted in the ScubaGear configuration file. |
| OrgUnitName | If applicable, an Agency’s bureau or subagency name. For example, “CISA” is the OrgUnitName for the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency. This is to be inserted in the ScubaGear configuration file, one level down from the top level. |
| PowerShell | A scripting platform developed by Microsoft. ScubaGear runs on PowerShell 5.1, and can be installed via PSGallery, a central repository for PowerShell modules. ScubaConnect also utilizes PowerShell scripts for onboarding and scanning. |
| Production Tenant/In-Scope | A CSP environment, primarily used by the government to conduct official government business, whether operated by the government or a contractor. BOD 25-01 applies to all production or operational cloud tenants (operating in or as federal information systems) with an associated and finalized SCuBA Secure Configuration Baselines published by CISA. |
| ScubaConnect | A cloud-native infrastructure application that automates the execution of the ScubaGear assessment tool across multiple tenants. |
| “Shall” Policies | “Shall” is to be interpreted as described in RFC 2119. “Shall” is an absolute requirement of the specification. |
| “Should” Policies | “Should” is to be interpreted as described in RFC 2119. “Should” means that there may exist valid reasons in particular circumstances to ignore a particular item, but the full implications must be understood and carefully weighed before choosing a different course. |
| Tenant ID | A dedicated identifier in the Azure Active Directory assigned to an organization when first registering for a Microsoft cloud service. To find your tenant ID, log into the Azure portal, click on “Azure Active Directory,” and then select “Properties.” |
| YAML File/Configuration File | YAML (the acronym for “YAML Ain’t Markup Language,” although it was originally the acronym for “Yet Another Markup Language”), is a human-readable data serialization language used in configuration (or “config”) files. Due to its simplicity, flexibility, and the ability to add comments, YAML is often used for configuration files compared to other languages, such as JSON. |
Appendix A: Sample Action Plan.csv Template
Below is an example of the CSV file template referenced in Requirement #6. This template is used to help agencies track why a policy is non-compliant, what will be done to meet compliance and an anticipated date for compliance.
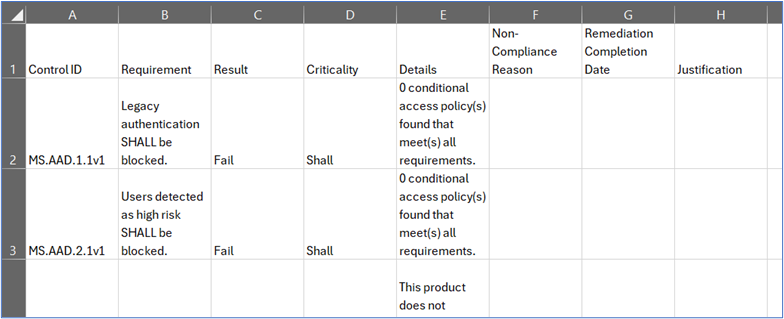
| Control ID |
A unique identifier assigned to each specific security policy within the Secure Configuration Baseline. Example: MS.TEAMS.1.6v1 refers to the policy recommending that meeting recording should be disabled. |
| Requirement |
The prescribed action or configuration setting that organizations should implement to enhance security. Example: For MS.TEAMS.1.6v1, the requirement is to disable meeting recording to prevent unauthorized disclosure of shared information. |
| Result |
The outcome of assessing whether the organization complies with the specified requirement. Example: If meeting recording is disabled as per MS.TEAMS.1.6v1, the result would be “Compliant.” |
| Criticality |
The level of importance or priority assigned to a control, indicating its impact on overall security. Example: Disabling meeting recording (MS.TEAMS.1.6v1) may be considered of high criticality due to the risk of unauthorized information disclosure. |
| Details |
Additional information or context about the control, including rationale, implementation notes, and references. Example: For MS.TEAMS.1.6v1, the details explain that disabling meeting recording limits information exposure and applies to both global and custom meeting policies. |
| Non-Compliance Reason |
The justification provided when a control is not implemented as recommended, often due to operational needs or exceptions. Example: An Agency might cite the need for recording meetings for legal documentation as a reason for not complying with MS.TEAMS.1.6v1. |
| Remediation Completion Date |
The target or actual date by which the organization plans to achieve compliance with the control. Example: An Agency may set December 31, 2025, as the remediation completion date for disabling meeting recording per MS.TEAMS.1.6v1. |
| Justification |
A detailed explanation supporting the decision to deviate from the recommended control, including risk assessments and compensating measures. Example: If an Agency continues to allow meeting recordings, the justification might include enhanced access controls and monitoring to mitigate associated risks. |
Appendix B: Manual Reporting in CyberScope
- Part 1: Submitting the Tenant Inventory
-
1. Accessing BOD 25-01 in CyberScope
Navigate to the CyberScope webpage where a user can access the BOD 25-01 section for submitting reports. Click on “BOD 25-01: Implementing Secure Practices for Cloud Services.”
2. Downloading the BOD 25-01 Reporting Template
Download the BOD 25-01 reporting template by clicking, “Download BOD 25-01: Implementing Secure Practices for Cloud Services Reporting Template.xlsx.”
3. Accessing the Tenant Inventory
Click “Open.”
4. Uploading the BOD 25-01 Reporting Template
After filling out the form, navigate to the upload page. Click “Choose File.”
5. Manually Populating the Tenant Inventory
Select “Add New Row.”
6. Saving Tenant Information
Verify that the information you uploaded is shown correctly, then click the “save” icon.
7. Reviewing the Saved Tenant Inventory
Verify that the information is correct according to your Agency.
- Part 2: Submitting Scan Results and Configuration Files
-
1. Drilling Into the Tenant Inventory
Click the right-facing chevron at the beginning of each row to open the submission section for the tenant.
2. Selecting the File Type and Uploading the File
For “Submission Type,” select “Scan Results” from the dropdown menu; then, click “Submit.”Do not alter the file name produced by the ScubaGear tool before submitting results to CyberScope. The file will have this pattern: ScubaResults_UUID.json, where the UUID is an 18-digit string of numbers and characters.

3. Reviewing Submitted Files
Select and submit the SCuBA assessment tool results by dragging and dropping the file or browsing and selecting the file. For the “Scan Results” requirement, the file type is limited to “.json” files. Grab and drop or select via browse the ScubaResults .json file in the output directory folder.
- Part 3: Data Validation
-
1. Navigating to the Validate/Approve Page
Navigate to the Validate/Approve page. Ensure that “S1: SCuBA-BOD.” is present.
2. Example of Errors to Be Resolved
Make note of or resolve any errors that may appear. If there are no errors, proceed to Step 3.
3. Approve/Locking with No Errors
To approve or lock the form, click on the “Approve/Lock Form” button.
4. Approved/Locked Verification
You will see a message showing confirmation of approval. If nothing more needs to be done to the form on your part, proceed to Part 4: Verifying Agency Contacts.
5. Reversing the Approve/Lock
If the form needs to be changed, click on the “Reopen/Unlock Form” button, then make adjustments and return to Step 2.
- Part 4: Verifying Agency Contacts
-
1. Attempting to Submit
Once all steps have been completed, click “Submit to CISA.”
2. Agency Contact Verification Message
Verify the agency contacts for the submission.
3. Navigating to Agency Contacts Page
Select the “Agency Contacts” tab.
4. Selecting the “Binding Operational Directive (BOD) Contact Type
On the “Type” dropdown, select “Binding Operational Directive (BOD).”
5. Entering Required Contact Information
Verify the correct contact information. If information needs to be changed, click on the pencil icon on the left to change the information in a row.
6. Saving Required Contact Information
Make any corrections in the fields, then click the checkmark to save.
7. Completing the Verifying Contacts Requirement
Once done, click “Verify Agency Contacts.”
8. Reviewing Verified Contacts
Review the results.
- Part 5: CyberScope Submission
-
1. Submitting the BOD 25-01 Report to CISA
To submit the BOD 25-01 report in CyberScope, click “Submit to CISA.”
2. Verifying the Submission
The submission should show a status of “Submitted on [date, time].” If a submission needs to be reopened, proceed to Step 3.
3. Reopening a Submission
To make changes to a submission, click “Reopen Submission,” and return to Step 1.
4. Reopened Submission Status
You will now see an updated status showing the date and time the submission was reopened. Once completed, click “Submit to CISA” to send the file to CISA.
Subscribe to SCuBA Email Updates

Stay up-to-date with the latest SCuBA updates.




