
Voluntary Cyber Incident Reporting
About this Resource
This page is designed to help entities that may be considering voluntarily reporting cyber incidents understand “who” CISA recommends report an incident, “why and when” CISA recommends they report, as well as “what and how to report.”
CISA asks every organization and entity that experiences a cyber incident report it to CISA.
Regardless of whether an organization is, or may later be, subject to regulatory cyber incident reporting requirements, reporting cyber incidents to CISA today benefits all of us across government and industry since cyber incidents have the potential to impact the economy, public health, and our national security. It also helps inform our collective understanding of the national cyber threat landscape. Cyber incident reporting:
- Enables rapid identification of ongoing incidents and increased understanding of successful mitigation measures, thereby increasing the ability of impacted entities and the Federal government to respond to ongoing campaigns faster and mitigate or minimize the consequences that could result from them.
- Facilitates the identification and sharing of information on exploited vulnerabilities and measures that can be taken to address those vulnerabilities, thereby enabling entities with un-remediated and unmitigated vulnerabilities on their systems to take steps to remedy or mitigate those vulnerabilities before they also fall victim.
- Supports CISA’s ability to share information to enable non-Federal and Federal partners to detect and counter sophisticated cyber campaigns earlier, with the potential to avoid or minimize negative impacts to critical infrastructure or national security, thereby reducing the risks associated with those campaigns.
- Contributes to a more accurate and comprehensive understanding of the cyber threat environment, allowing CISA’s Federal and non-Federal stakeholders to more efficiently and effectively allocate resources to prevent, deter, defend against, respond to, and mitigate significant cyber threats.
- Supports sharing of information about common threat actor tactics, techniques, and procedures with the information technology community, enabling software developers and vendors to develop more secure products or send out updates to add security to existing products, better protecting end users.
- Allows law enforcement entities to use reported information to investigate, identify, and prosecute perpetrators of cybercrime, getting malicious cyber actors off the street and deterring future actors.
- Enhances CISA’s ability to identify trends and track cyber threat activity across the cyber threat landscape beyond the Federal agencies that are required to report information to CISA.
Our lives and our work have become increasingly digitized. Web-enabled services and inter-connected devices offer significant efficiencies but also increase exposure to cyber actors seeking to exploit vulnerabilities. Today, nation-state backed cyber actors, cyber criminals, and other threat actors have much wider opportunities to sneak into networks and steal or ransom sensitive information and critical data, position themselves to disrupt service at a time of their choosing, and otherwise wreak havoc. Compounding the risk is rapidly advancing technology like artificial intelligence, which can make it faster and easier for adversaries to conduct cyber incidents.
See it in Action!
Check out this animation to see how reporting what you see can help build a comprehensive understanding of the threat and offer decisionmakers clues on how to stop the threat.
Ready to Voluntarily Report a Cyber Incident?
CISA’s reporting form is designed to help CISA understand what is happening in the cyber threat landscape. Before you click the Report button, these types of information will be helpful to have on hand:
- Identity of the impacted entity
- Contact information for the impacted entity
- Description of the incident, including information such as:
- A description of the vulnerabilities exploited
- Explanation of the tactics, techniques, and procedures leveraged by the adversary
- A description on how the incident was discovered
- Details on the impact to your organization
- Details on the impact to the services or goods your organization provides to others
- Details on any impact to life and safety
- Technical indicators and artifacts associated with the incident such as:
- Indicators of compromise (ex: malware hashes, IP addresses, domain names, URLs, email addresses, phishing emails or other messages), which can be submitted with your incident report
- Malware or files suspected of containing or being malware, which can be submitted via the “Report Malware” [fill in whatever word is added to toolkit] within the CISA Services Portal
- Steps taken to mitigate and/or respond to the incident, including an assessment of the effectiveness of such actions
CISA encourages organizations to submit a report immediately with information that is available and understood at the time, and then to return to your incident report as you have new information to provide updates.
Voluntarily Report a Cyber Incident
Resources to Help Reduce Your Cyber Risk
Incident reporting—while critical—is just one piece of the cybersecurity picture. The information and tools below offer some key ways to boost organization’s cyber capabilities, stay informed on current threats and mitigation steps, prepare for cyber risks from emerging technology, and more.

Secure Our World
The Secure Our World program offers resources and advice to stay safe online. Each of us has a part to play in keeping ourselves and others safe. It’s easy to do and takes less time than you think!

Free Cybersecurity Services and Tools
In addition to offering a range of no-cost CISA-provided cybersecurity services, CISA has compiled a list of free services and tools provided by private and public sector organizations across the cyber community.

Known Exploited Vulnerabilities Catalog
CISA maintains the authoritative source of vulnerabilities that have been exploited in the wild. Organizations should use the KEV catalog as an input to their vulnerability management prioritization framework.

Cybersecurity Alerts & Advisories
CISA regularly issues Cybersecurity Advisories, which are in-depth reports covering a specific cybersecurity issue, often including threat actor tactics, techniques, and procedures; indicators of compromise; and mitigations.

Secure by Design
It's time to build cybersecurity into the design and manufacture of technology products. Find out here what it means to be secure by design.

Cybersecurity Performance Goals
A common set of protections that all critical infrastructure entities - from large to small - should implement to meaningfully reduce the likelihood and impact of known risks and adversary techniques.

Shields Ready
Shields Ready is about making resilience during incidents a reality by taking action before incidents occur. A companion to Shields Up, Shields Ready drives action at the intersection of critical infrastructure resilience and national preparedness.
Artificial Intelligence
As the nation’s cyber defense agency and the national coordinator for critical infrastructure security and resilience, CISA will play a key role in addressing and managing risks at the nexus of AI, cybersecurity, and critical infrastructure.
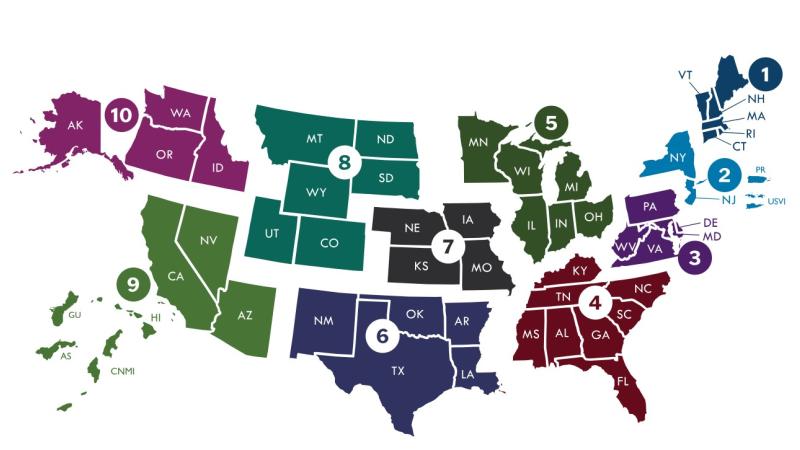
CISA Regions
CISA has 10 regional offices across the nation with personnel who collaborate with and offer a range of cyber and physical services to critical infrastructure partners and communities at the regional, state, county, tribal, and local levels.

CISA Cyber Hygiene Services
Take advantage of CISA’s Cyber Hygiene services to significantly reduce risk, avoid surprises, sharpen your response, and broaden your security horizon. CISA's Cyber Hygiene services include vulnerability scanning and web application scanning.
Cyber Incident Reporting for Critical Infrastructure Act of 2022 (CIRCIA)
In March 2022, President Biden signed into law the Cyber Incident Reporting for Critical Infrastructure Act of 2022 (CIRCIA). Enactment of CIRCIA marked an important milestone in improving America’s cybersecurity by, among other things, requiring the Cybersecurity and Infrastructure Security Agency (CISA) to develop and implement regulations requiring covered entities to report covered cyber incidents and ransomware payments to CISA. These reports will allow CISA to rapidly deploy resources and render assistance to victims suffering attacks, analyze incoming reporting across sectors to spot trends, and quickly share that information with network defenders to warn other potential victims.




